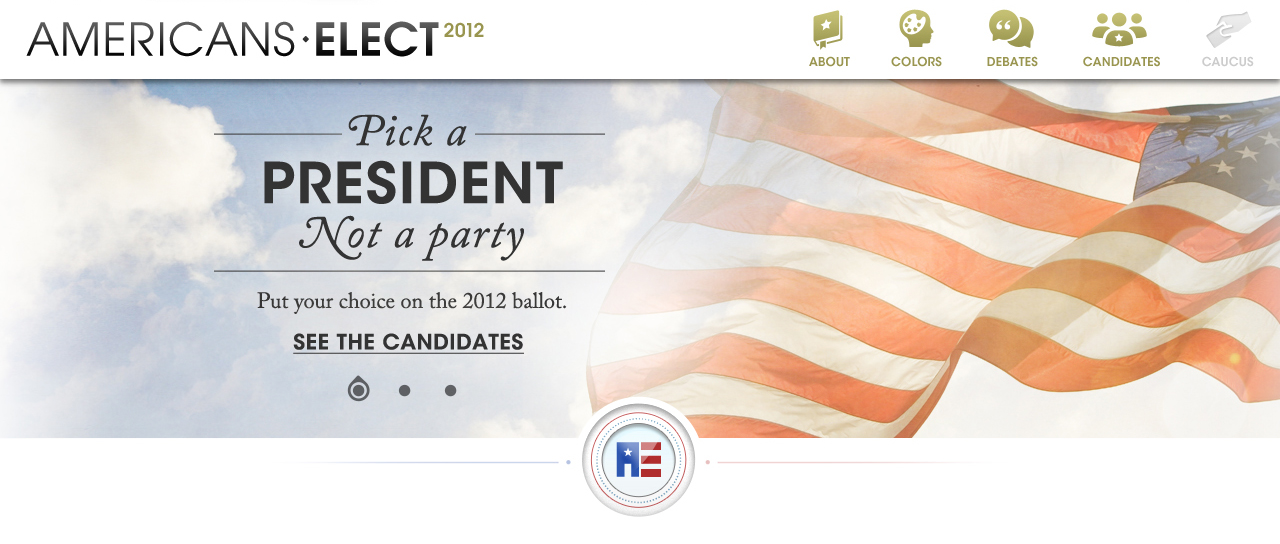
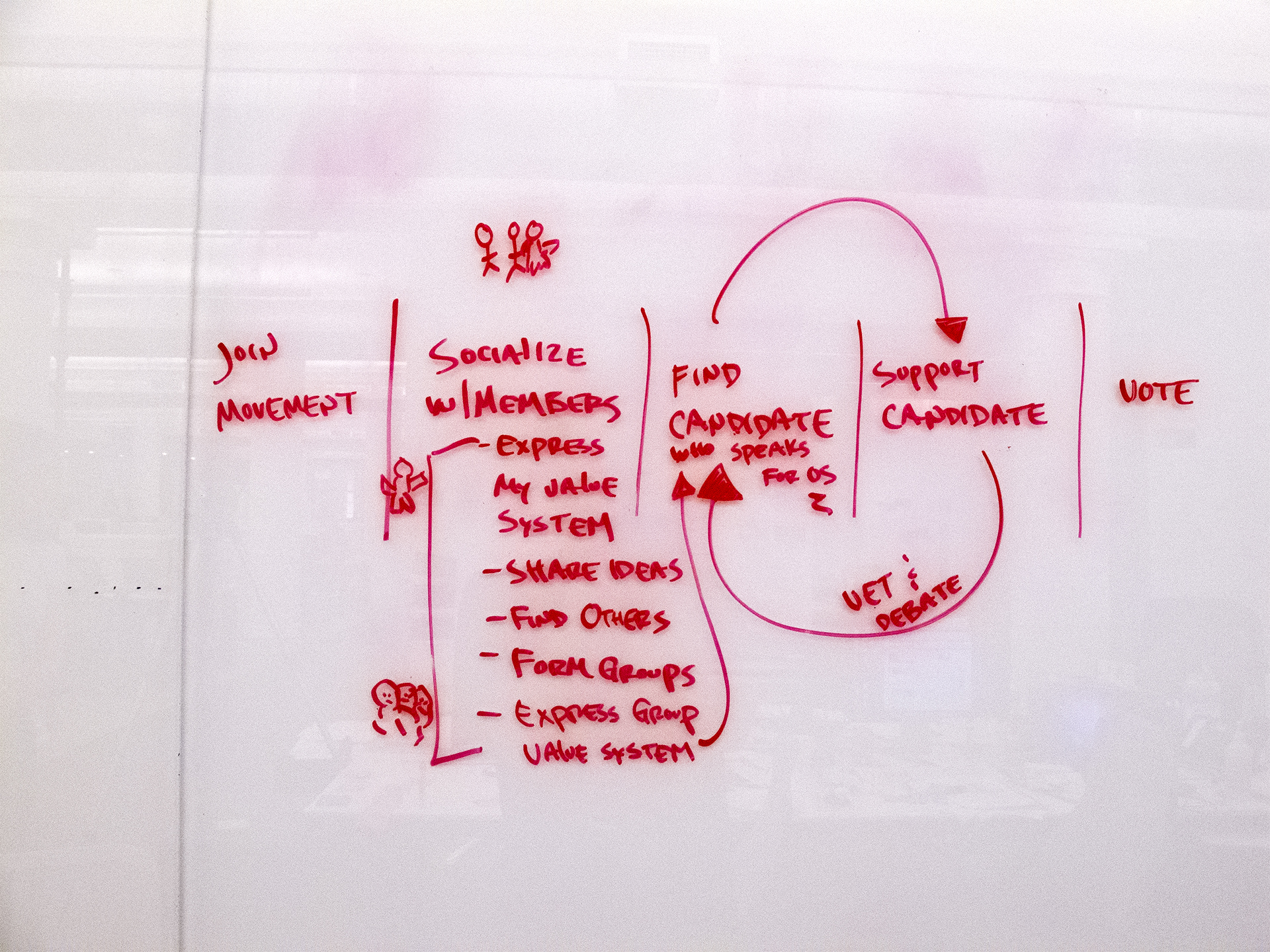
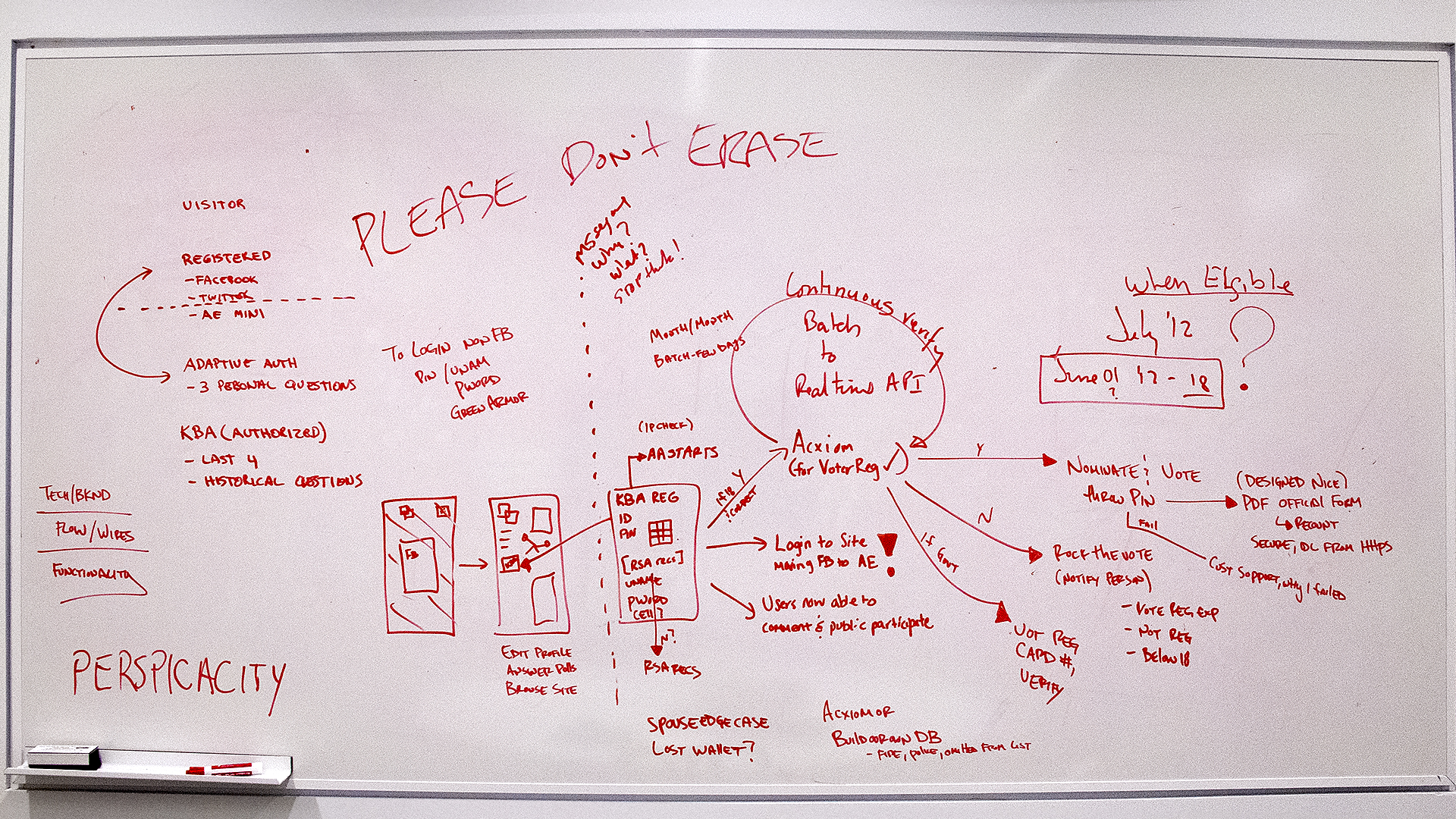
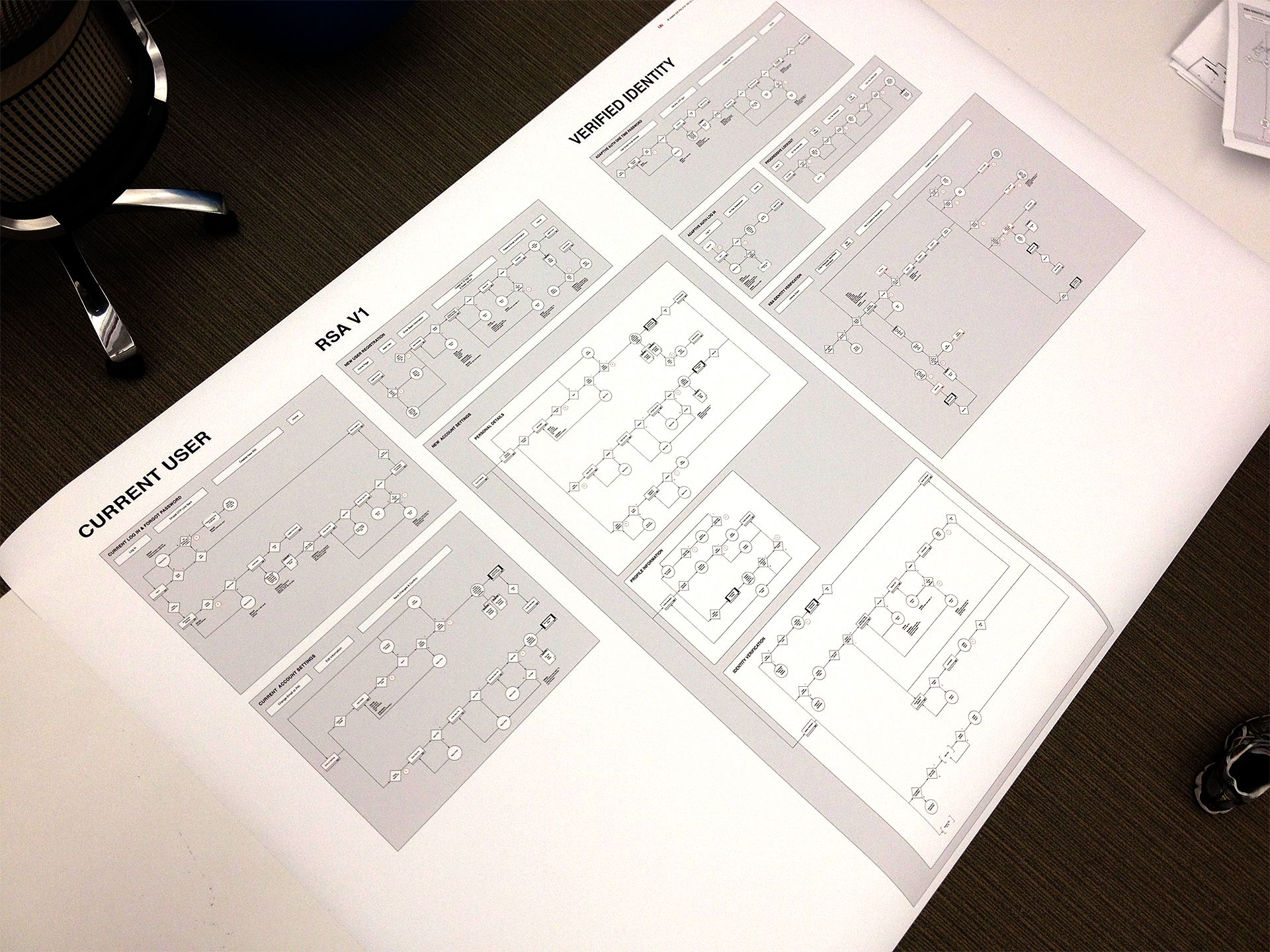
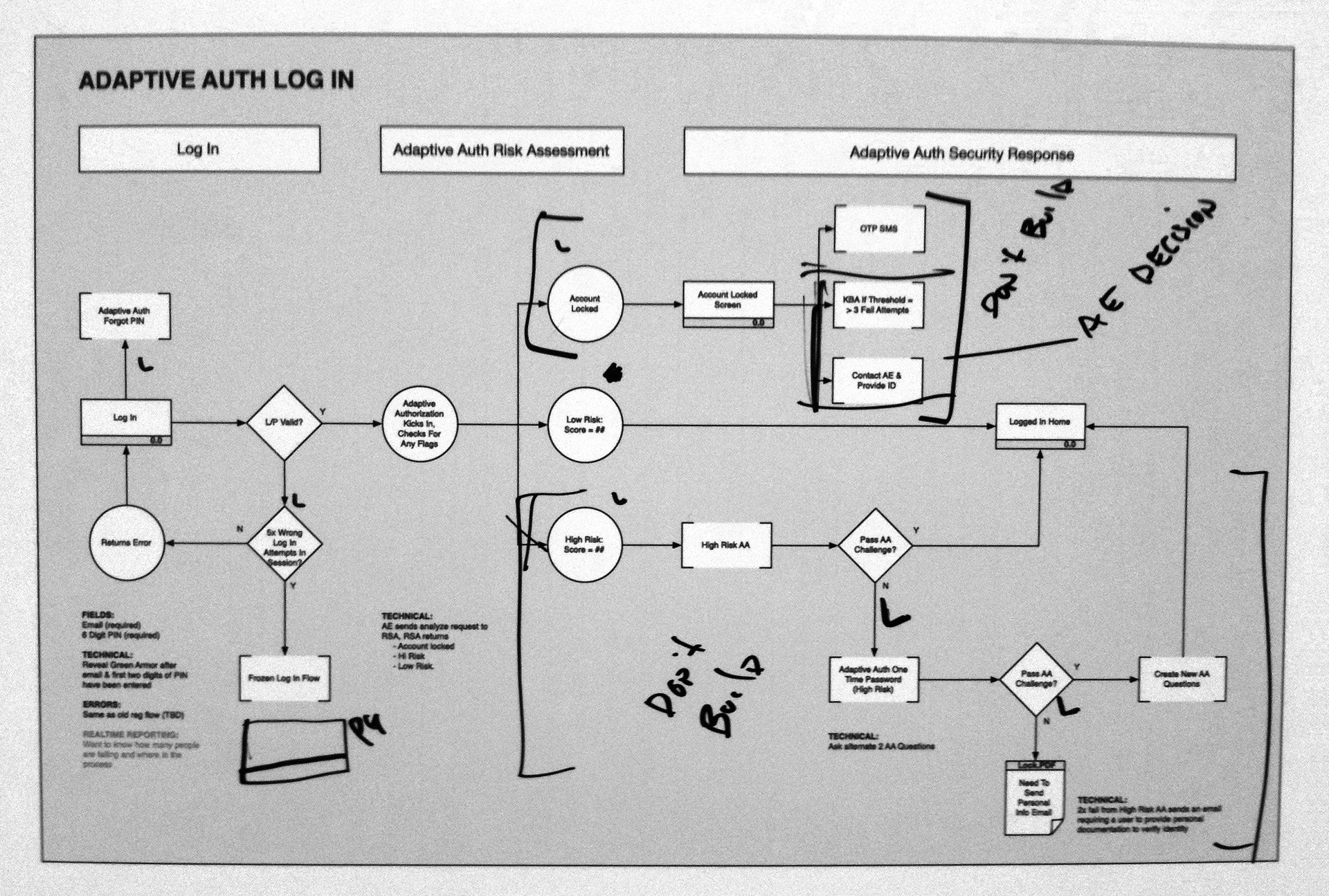
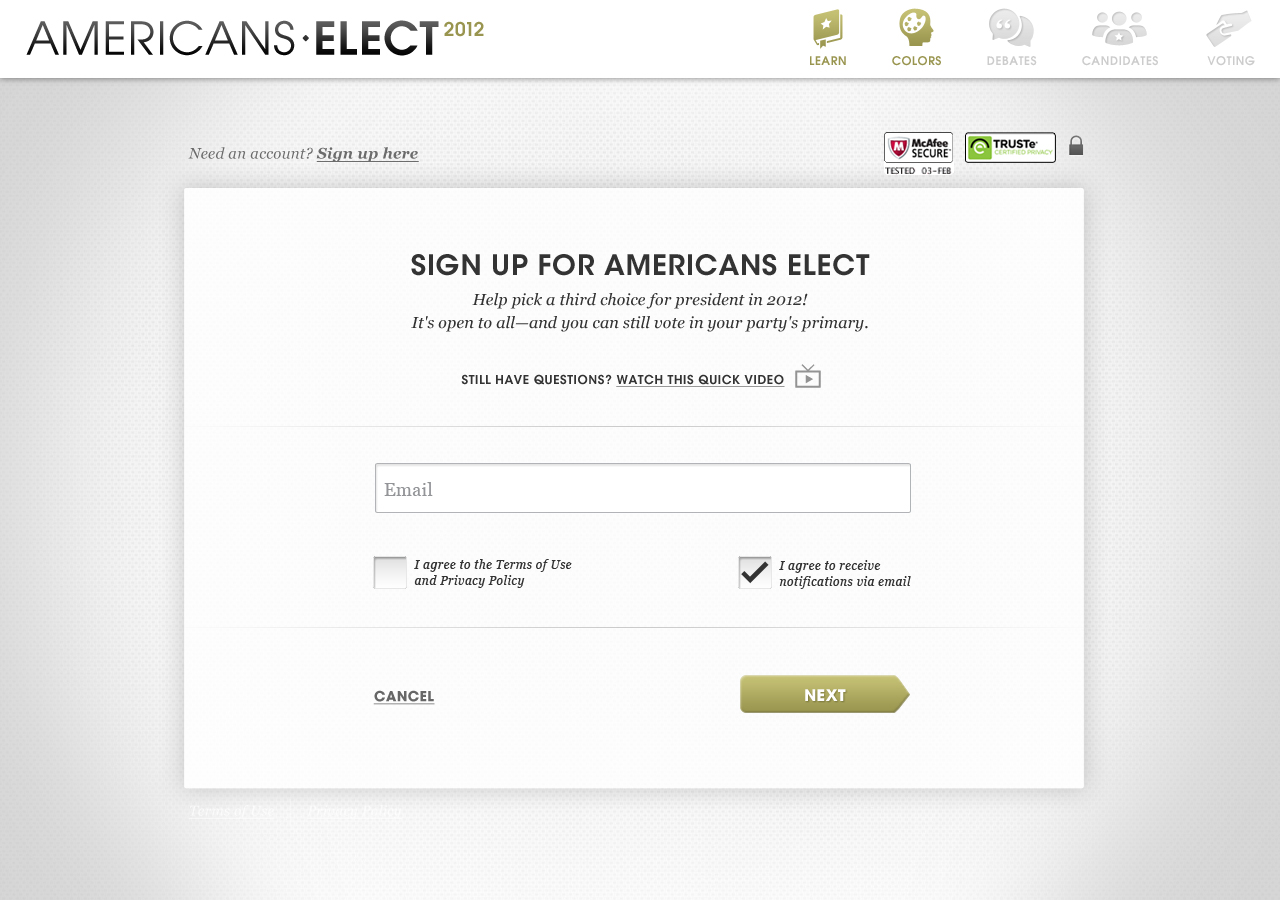
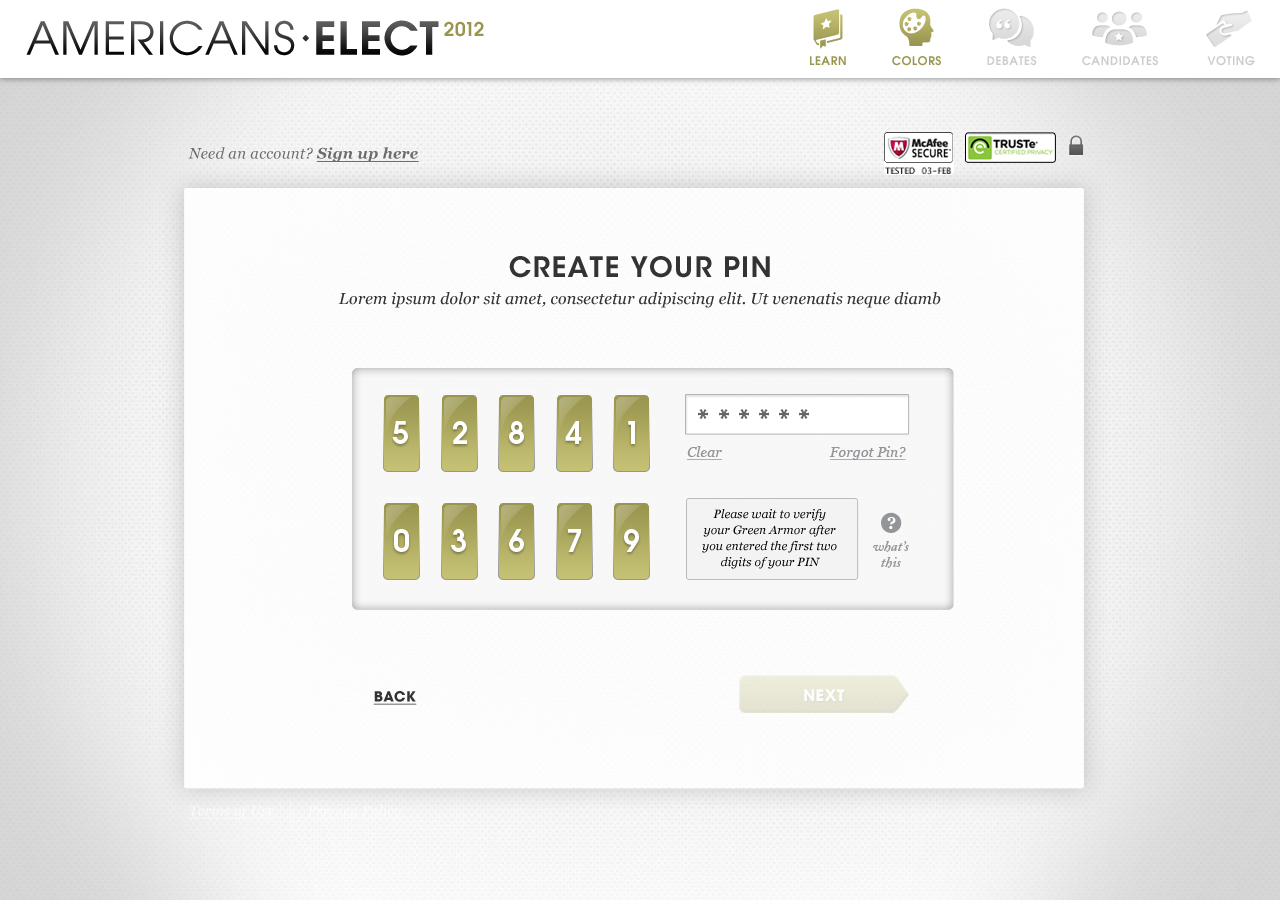
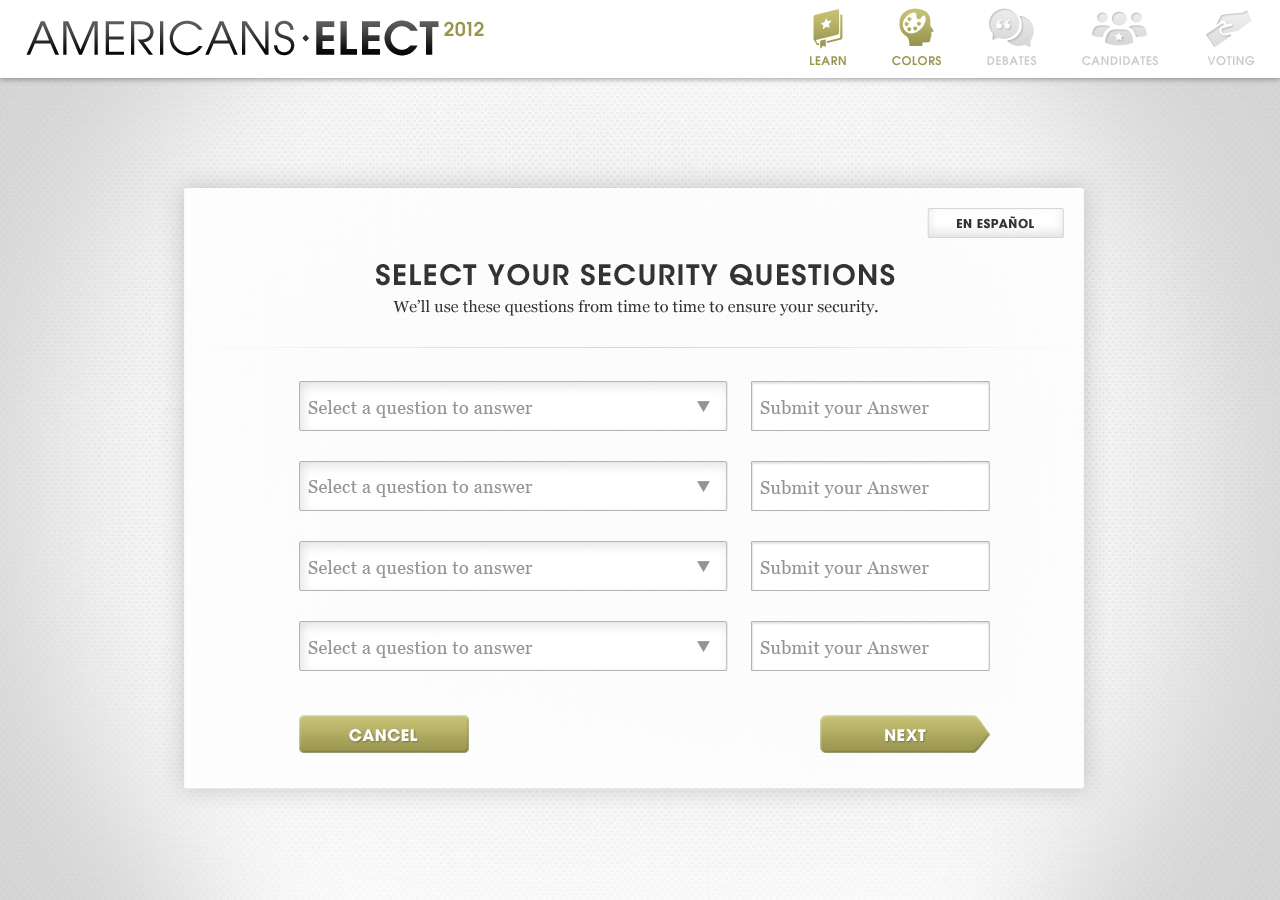
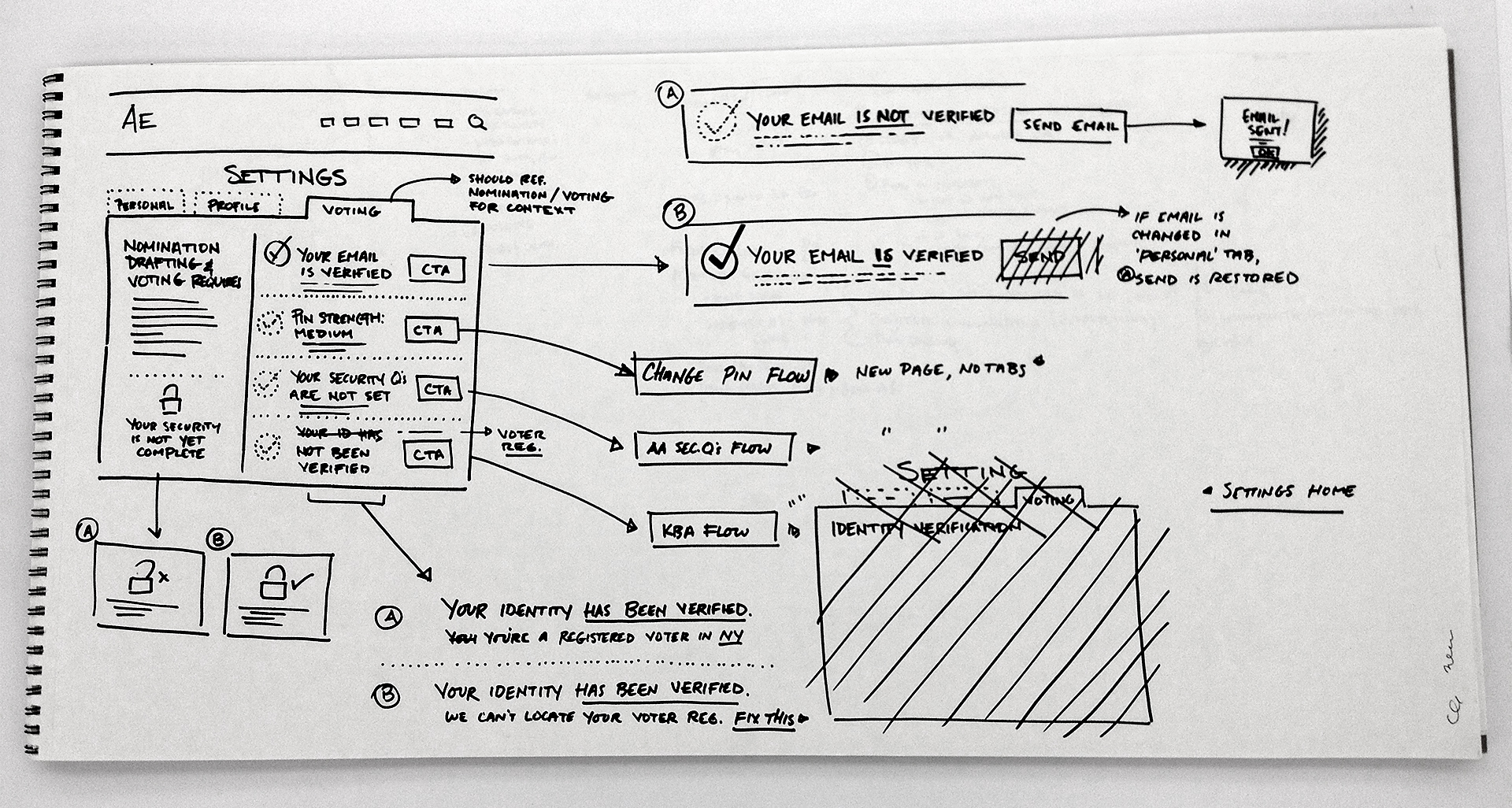
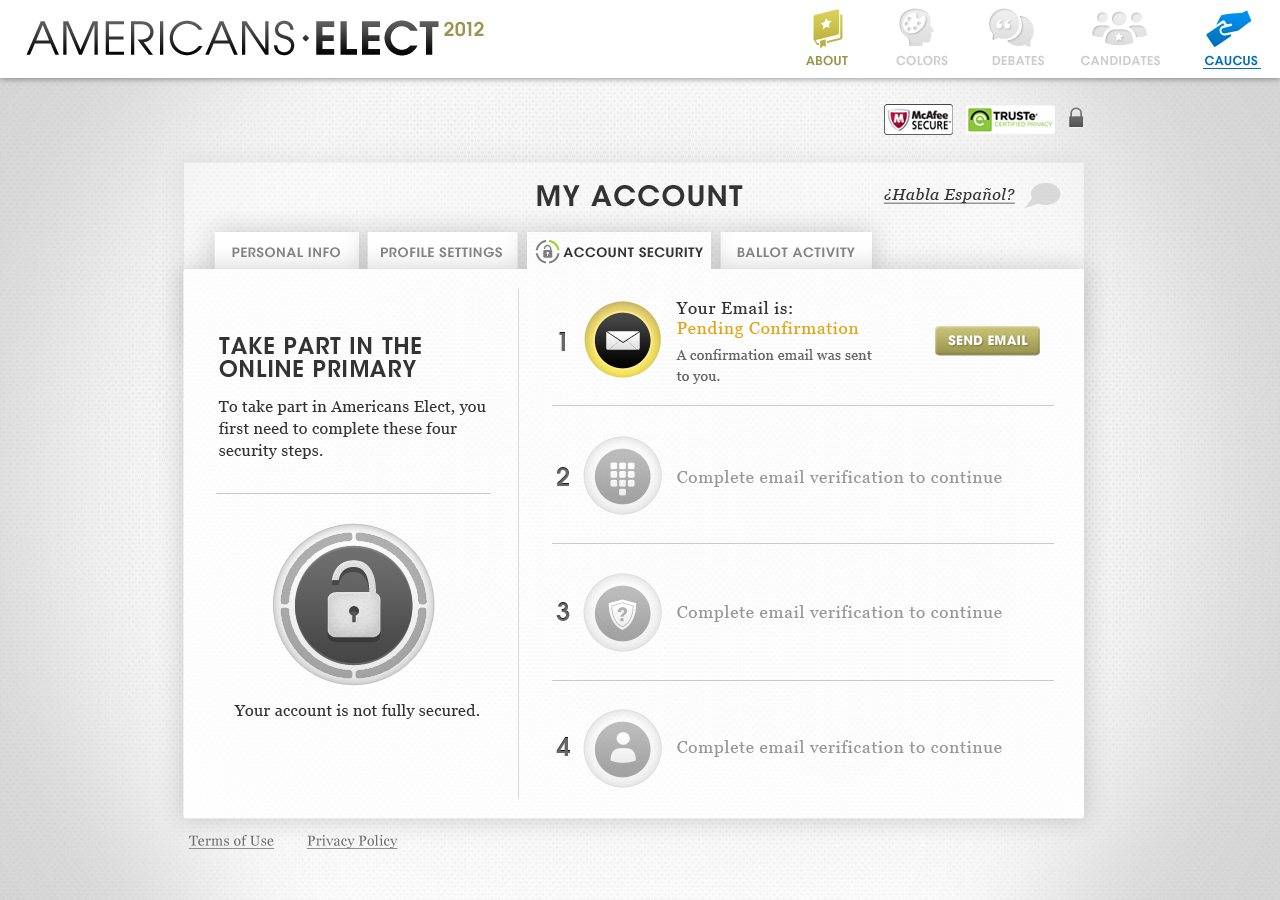
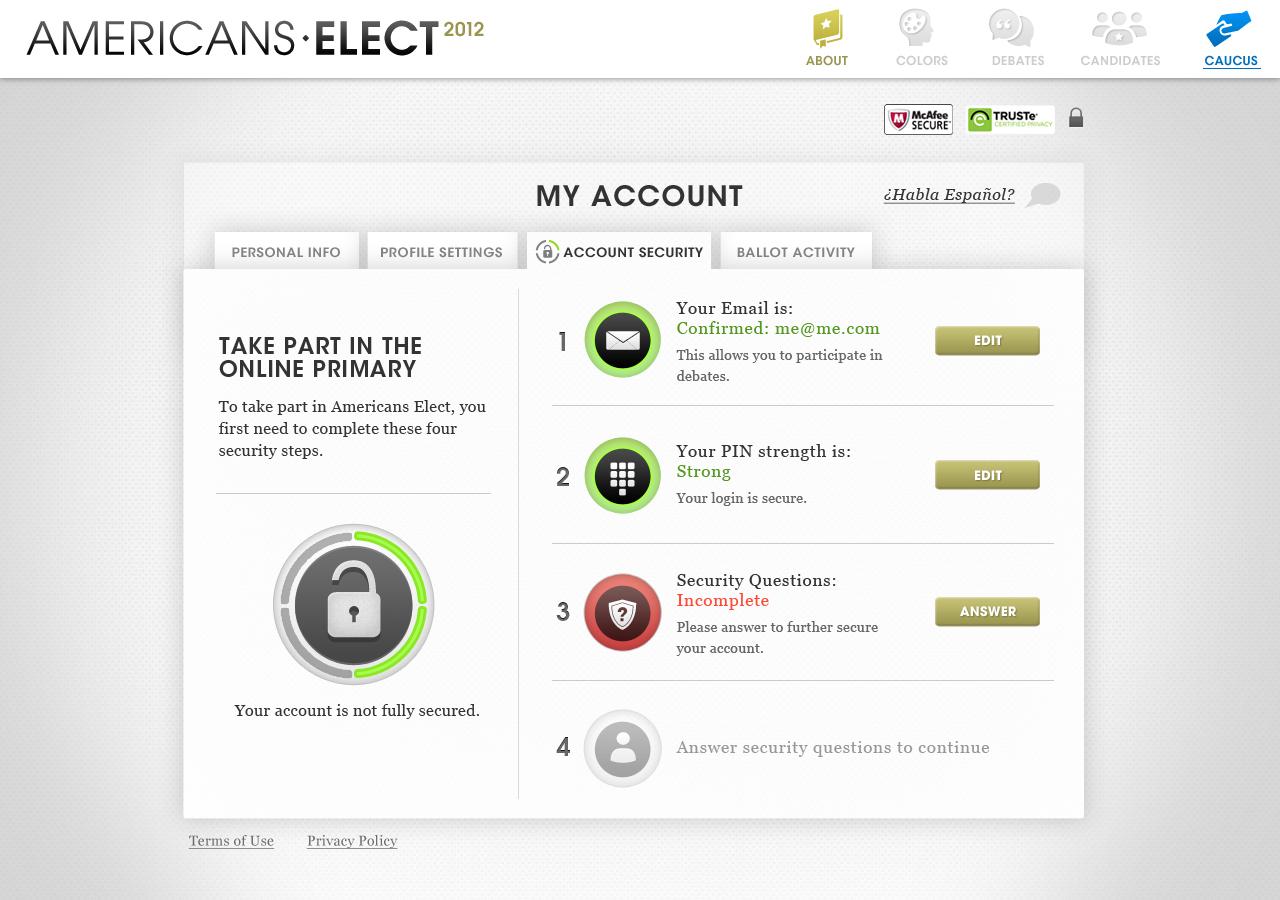
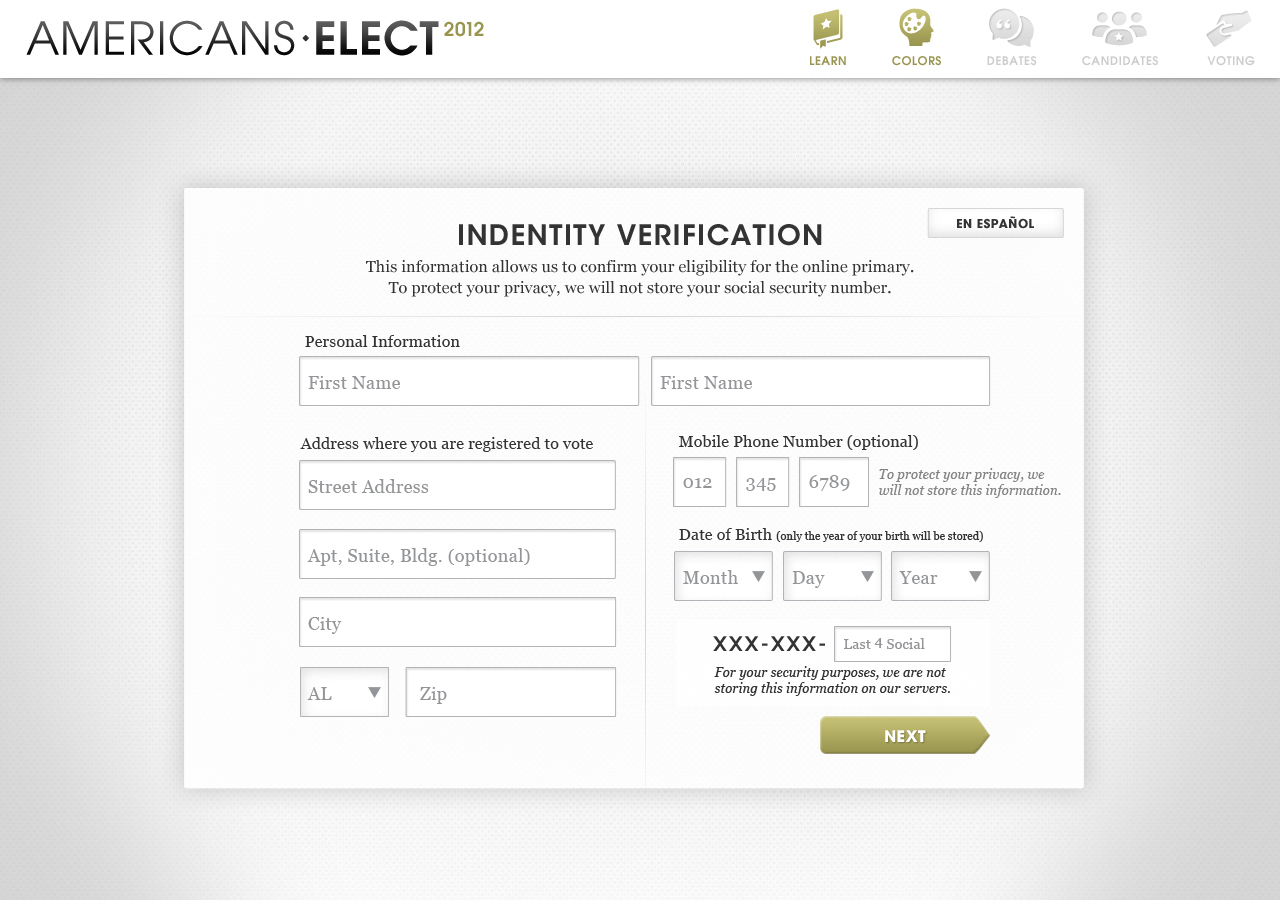
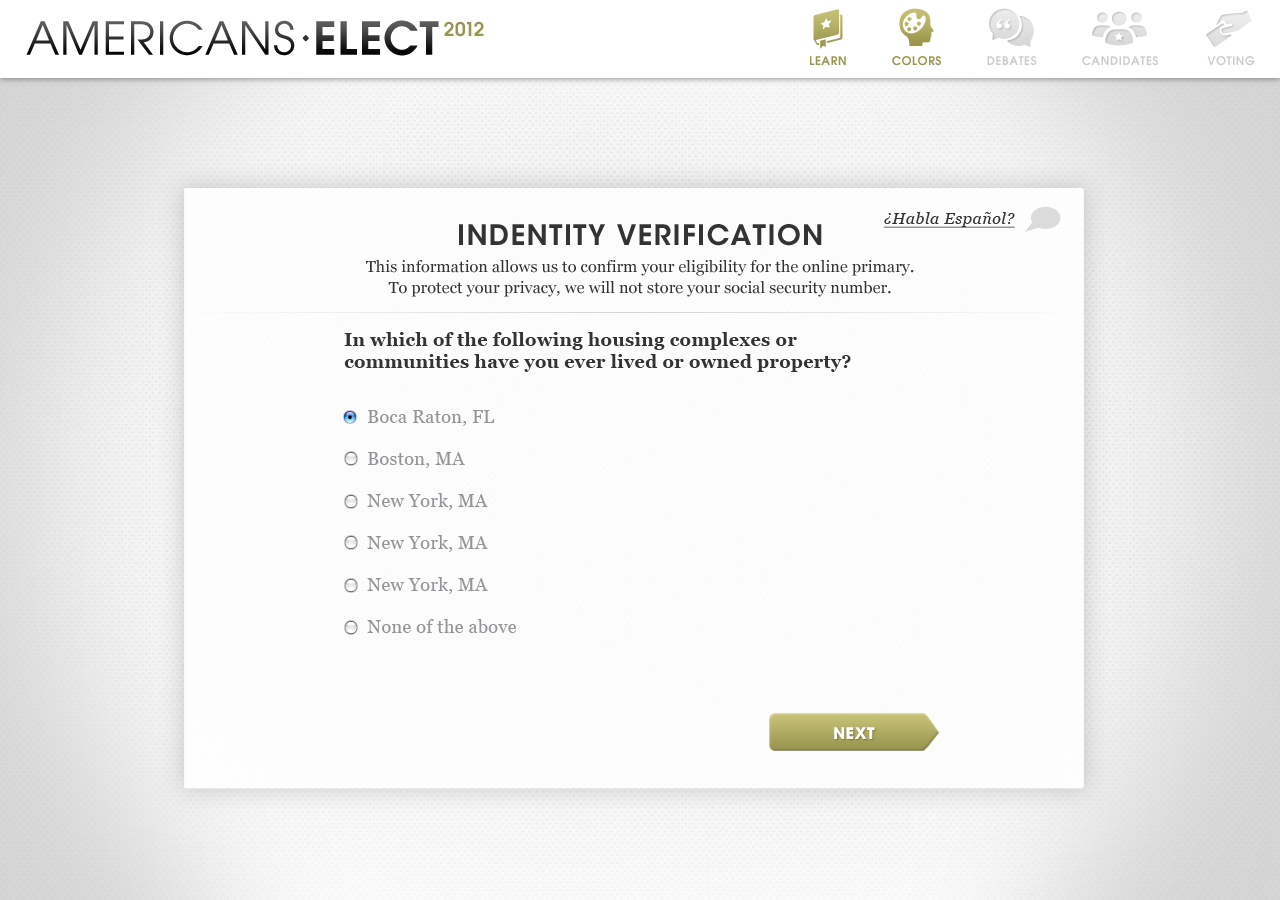
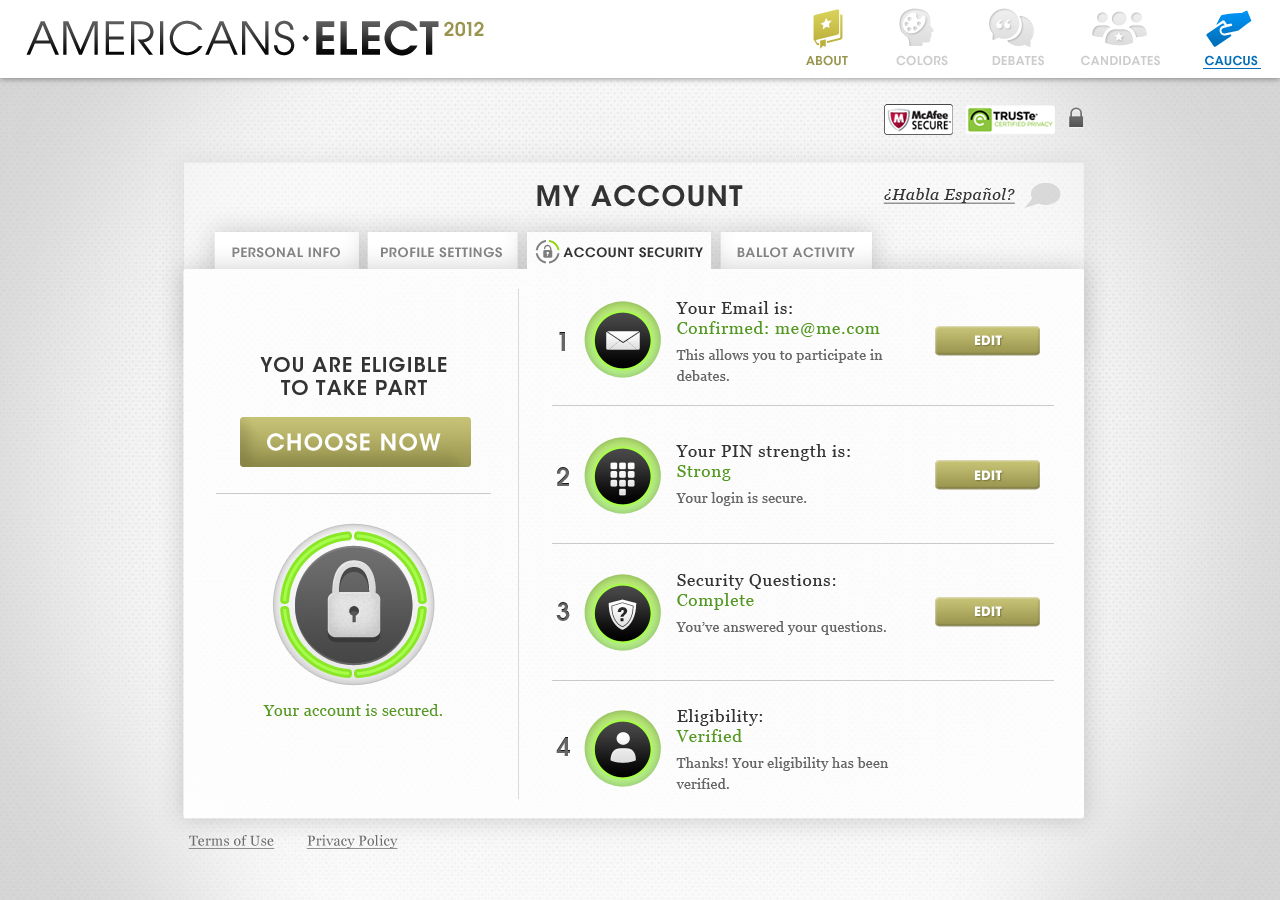
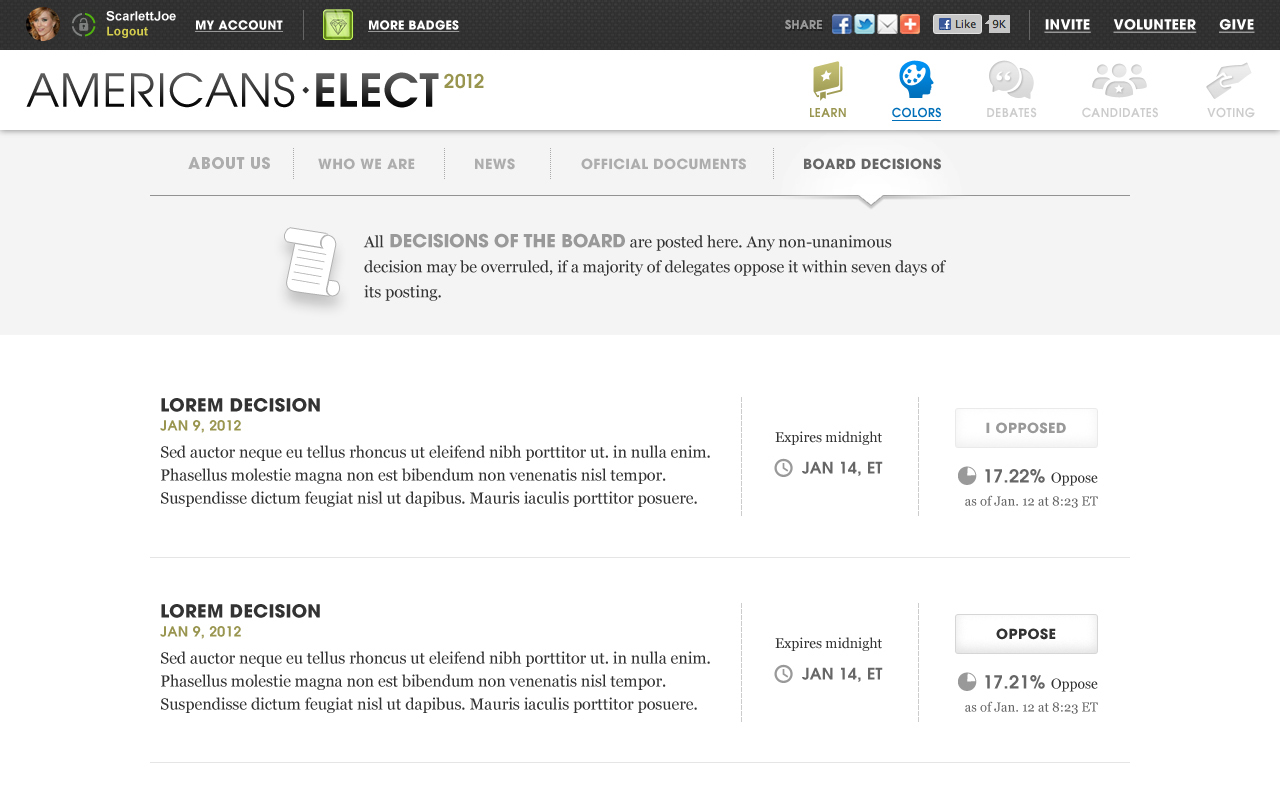
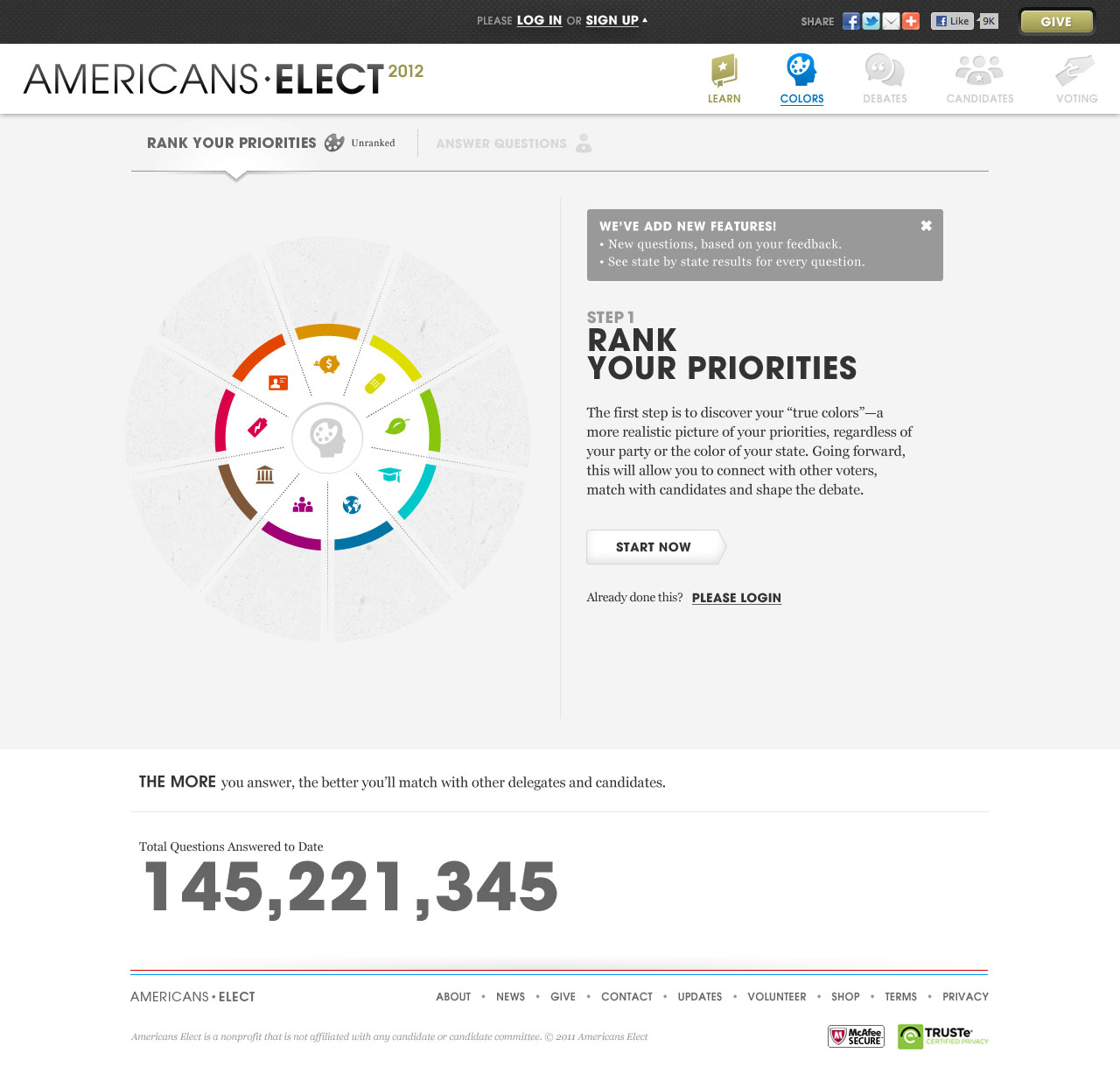
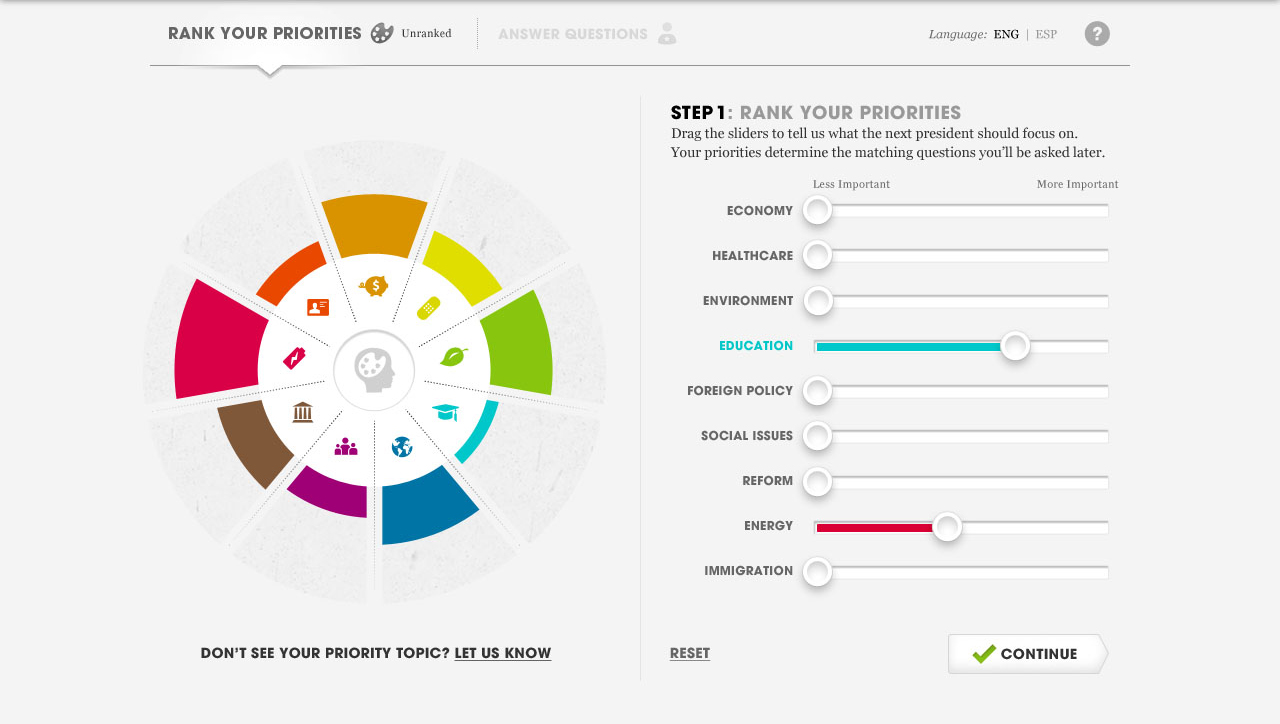
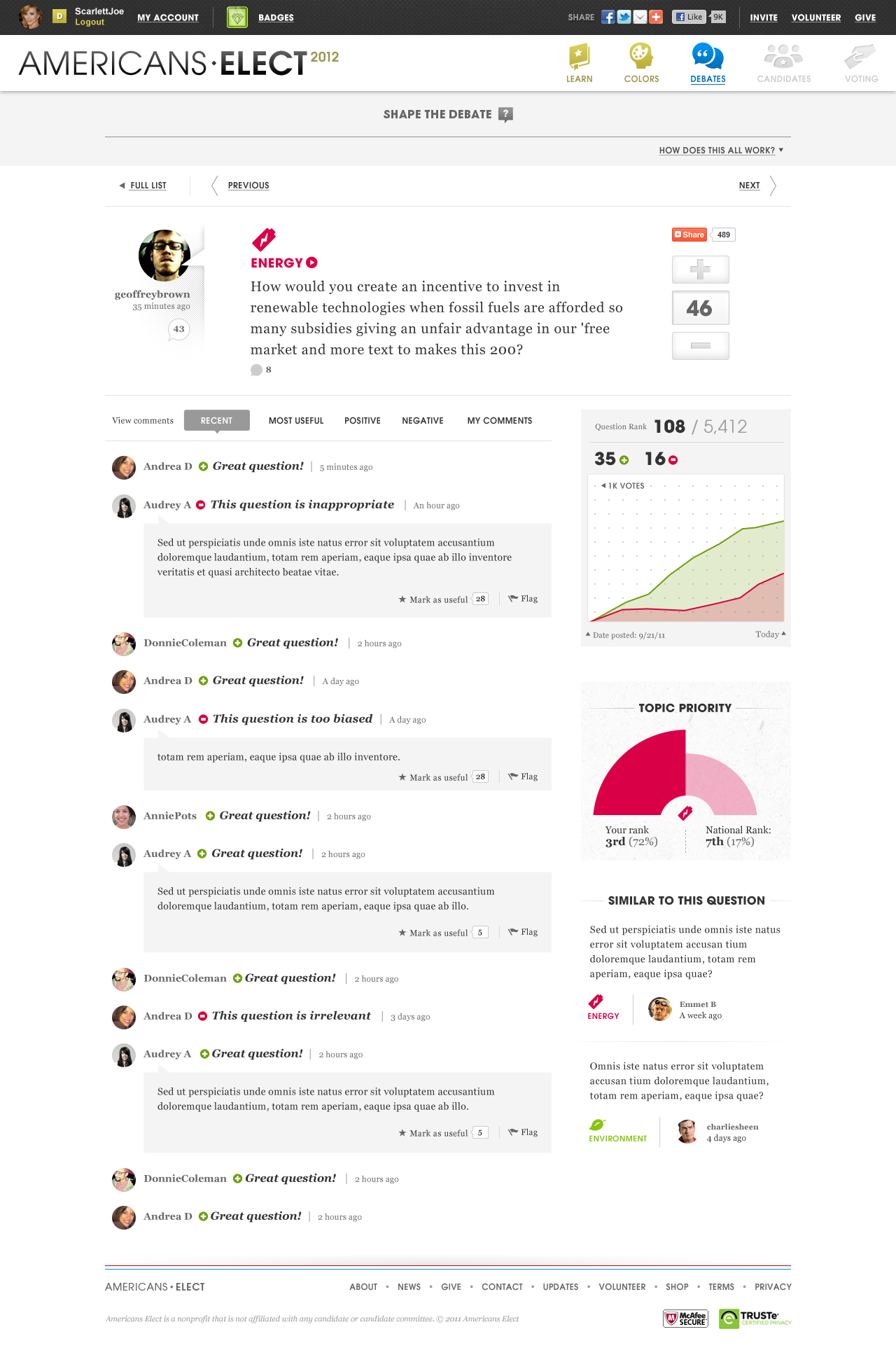
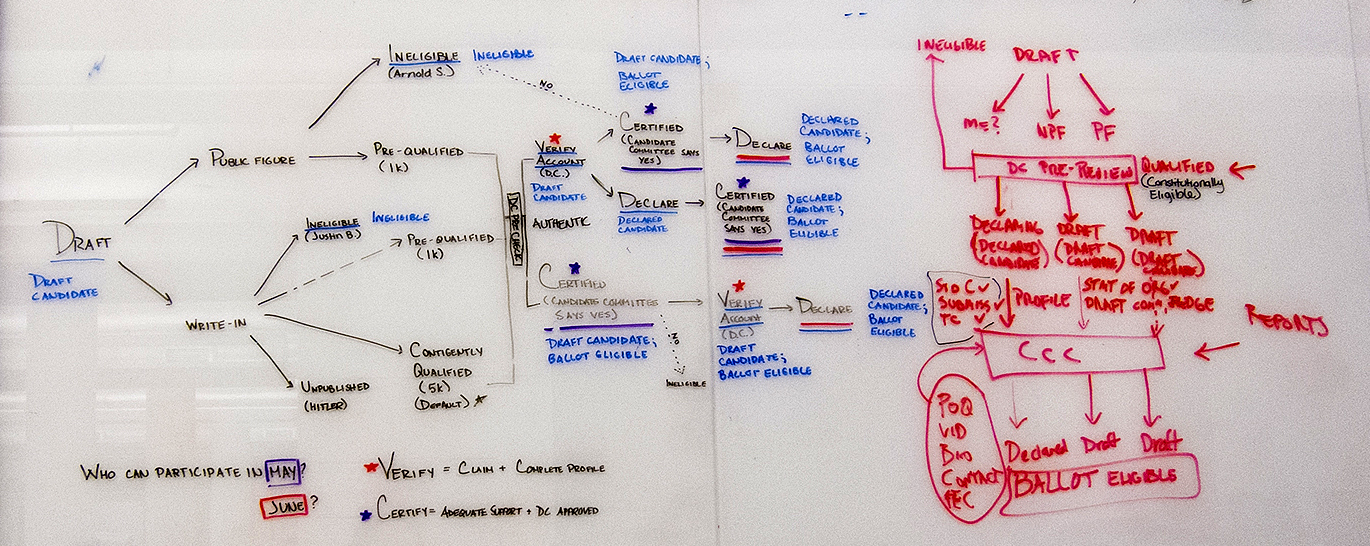
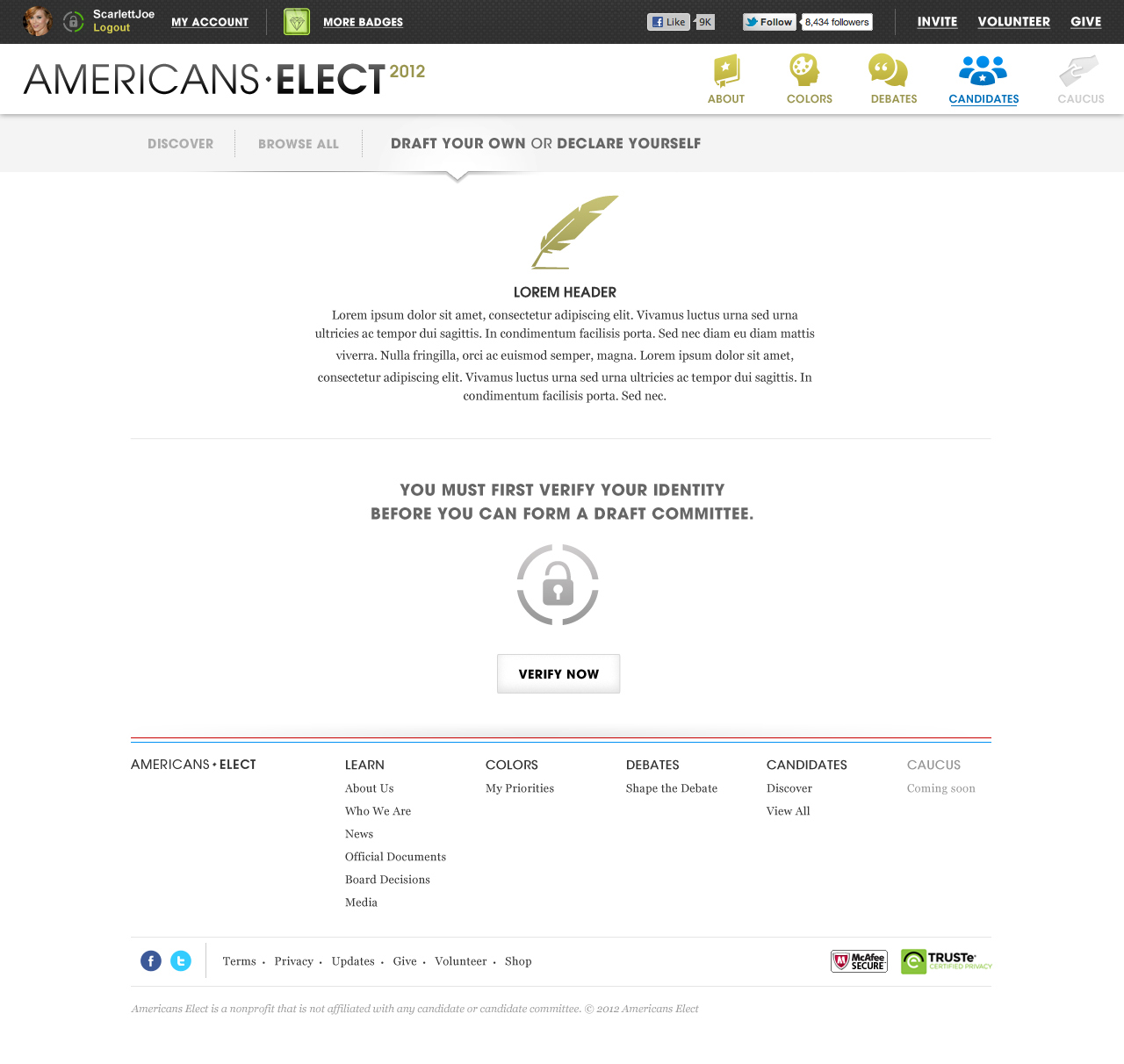
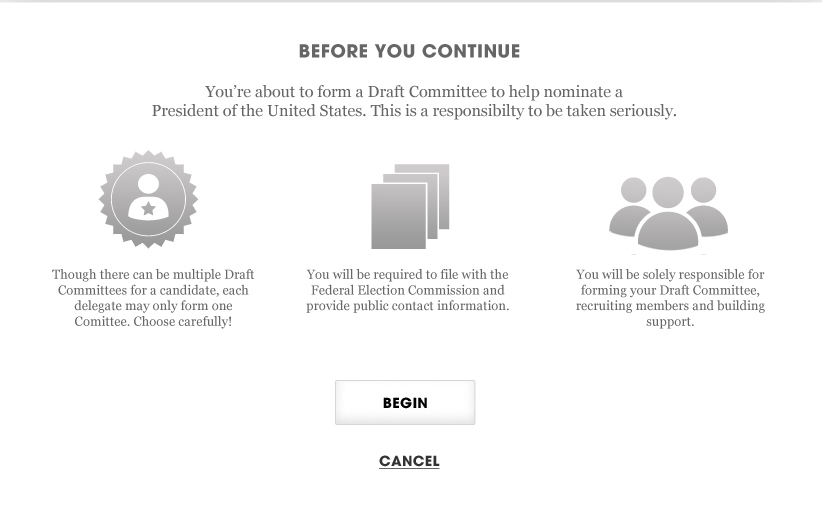
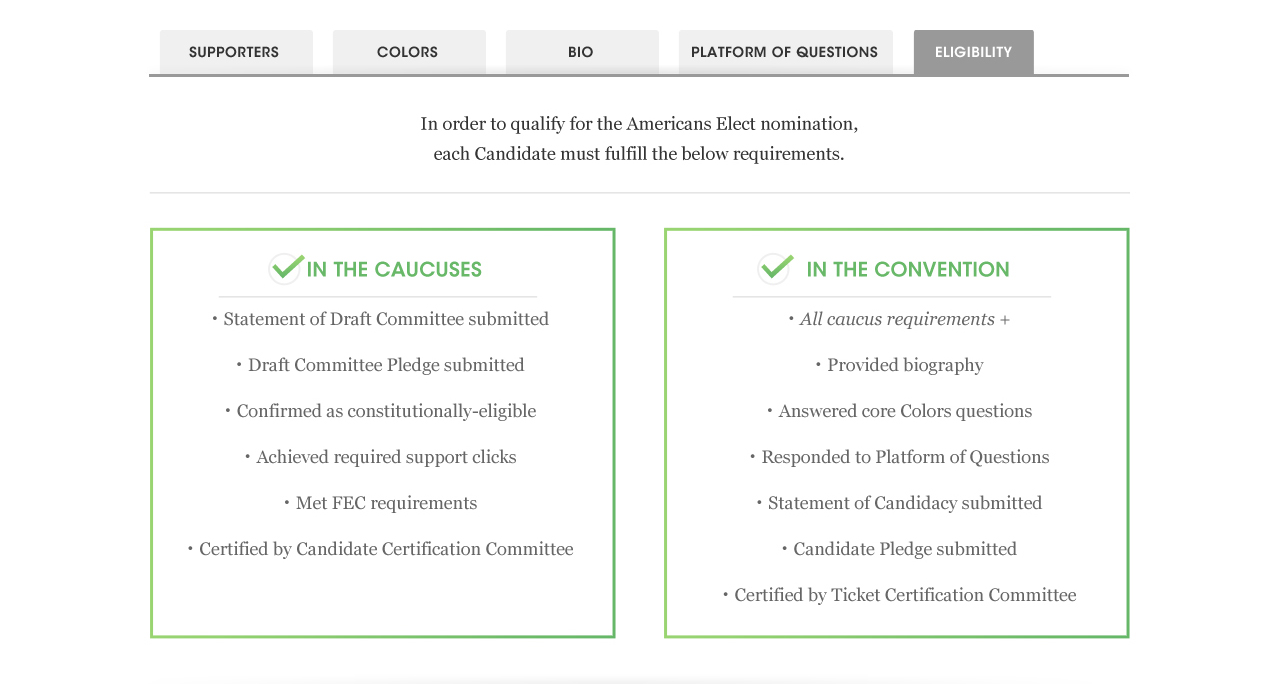
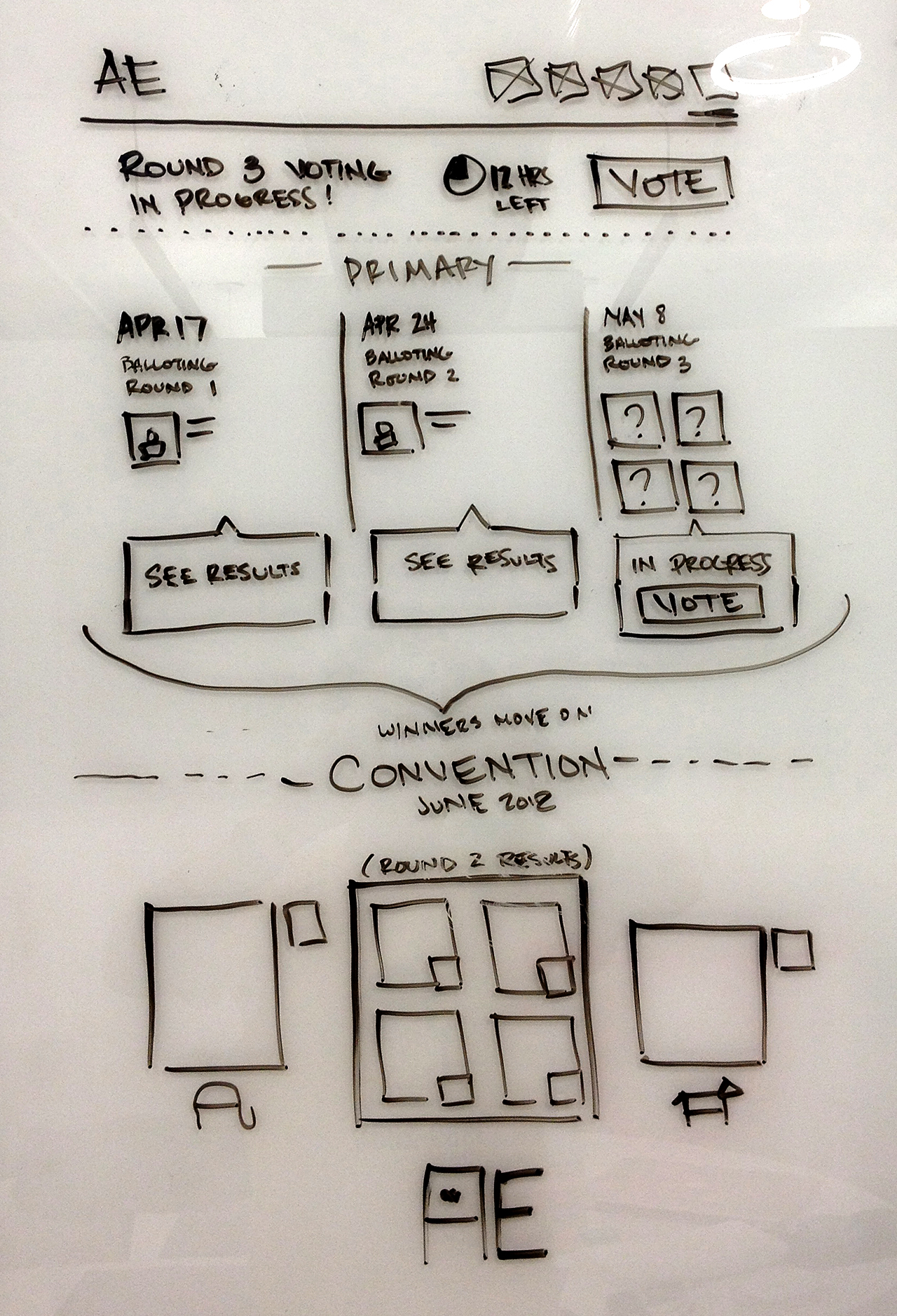
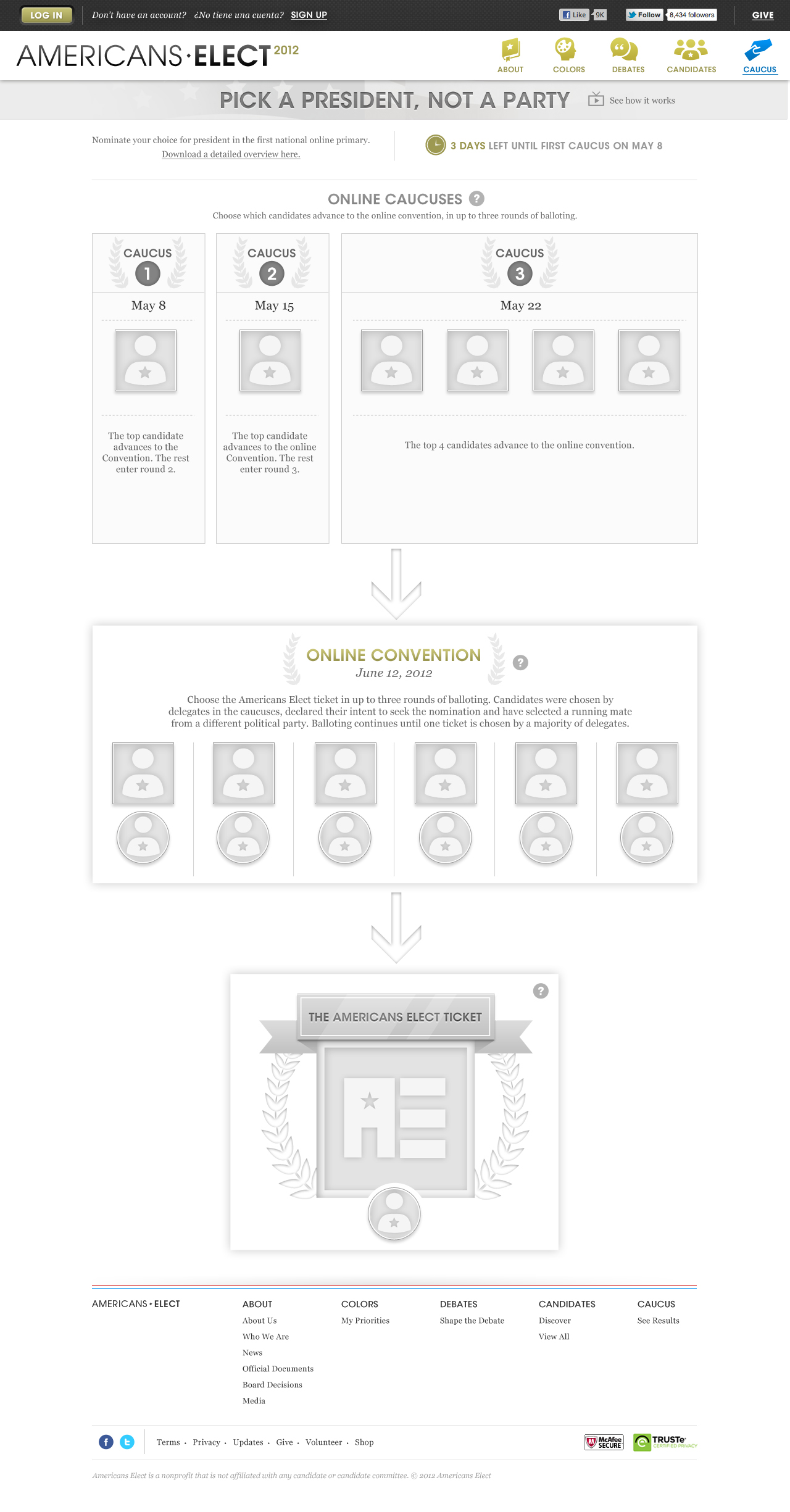
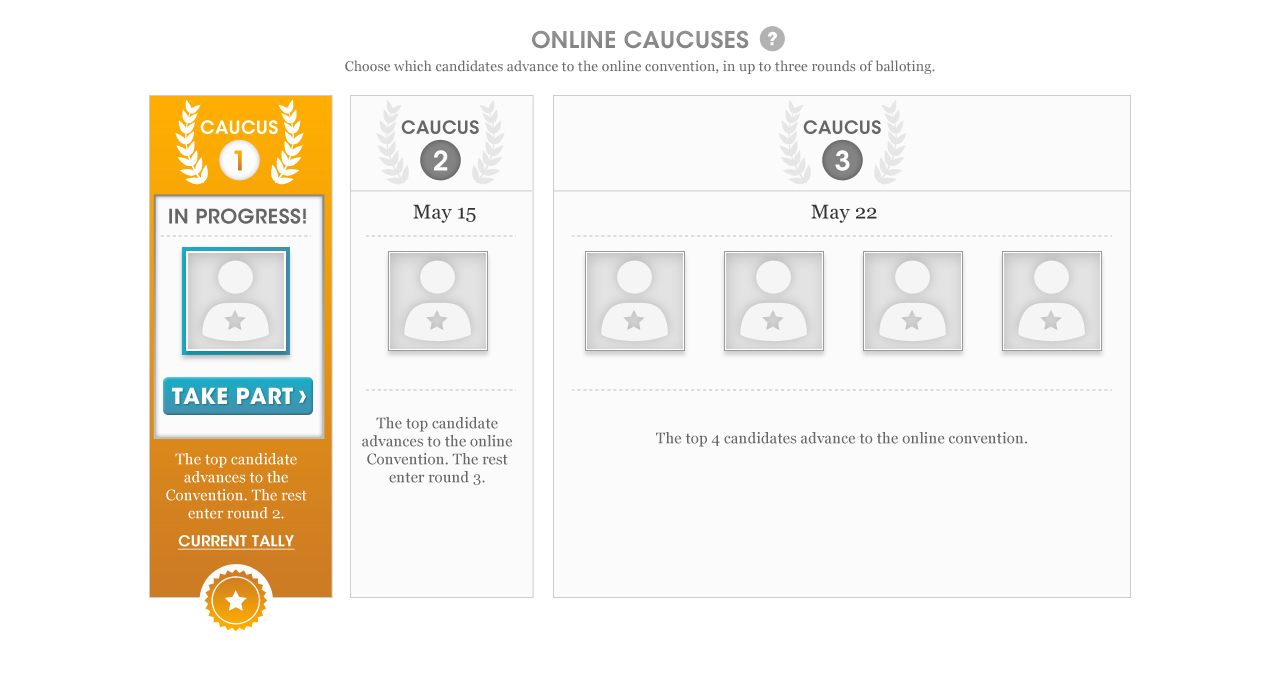
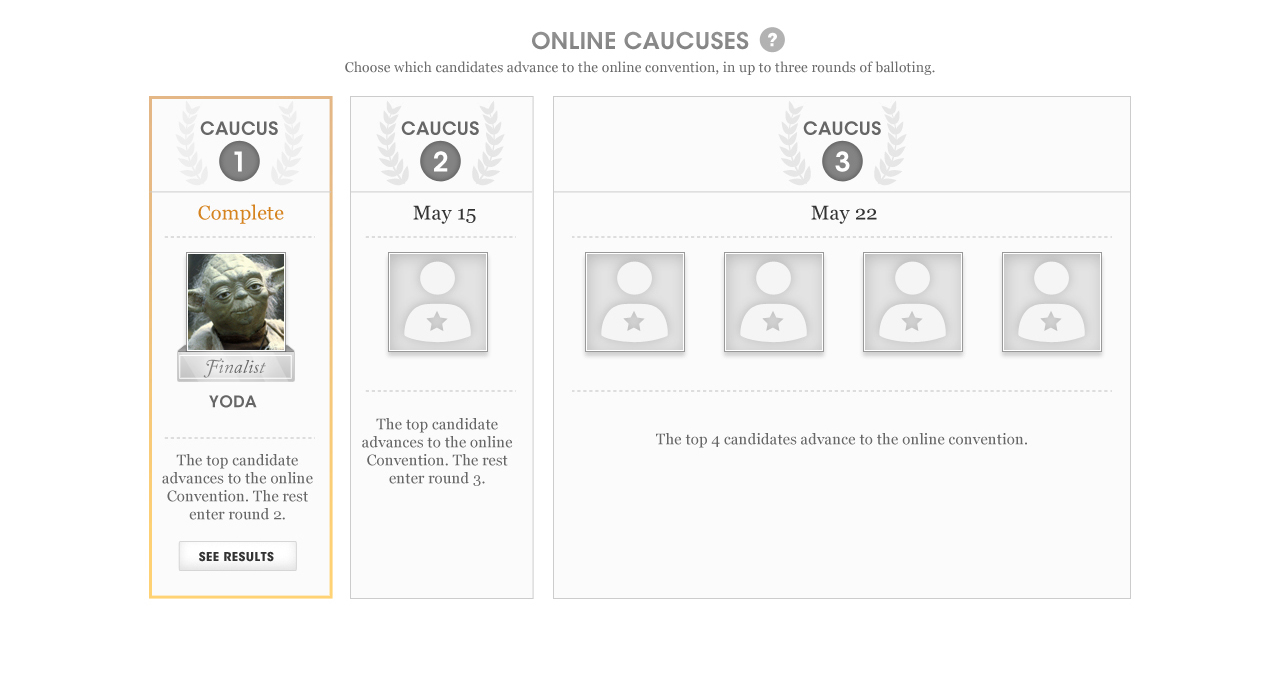
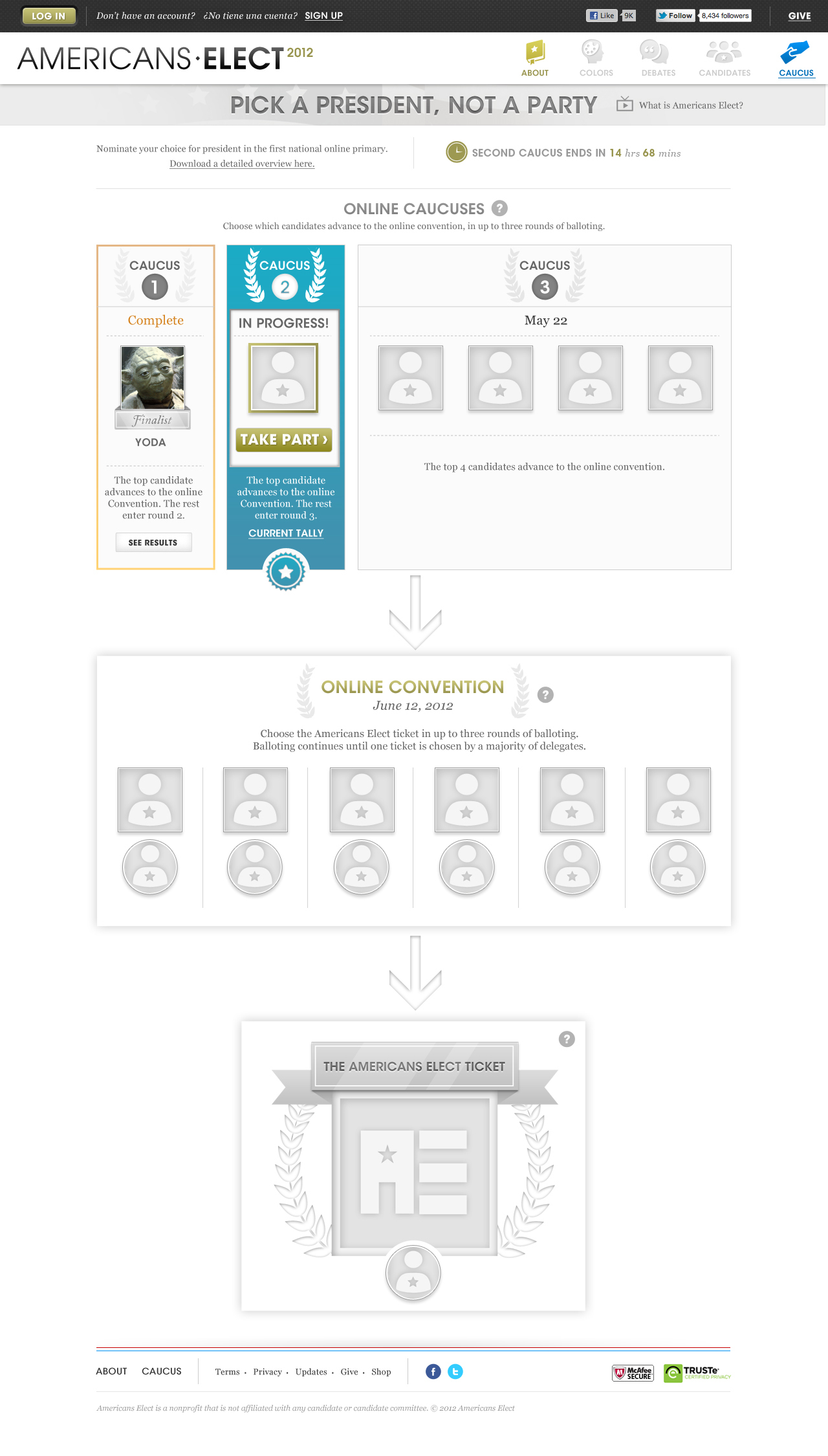
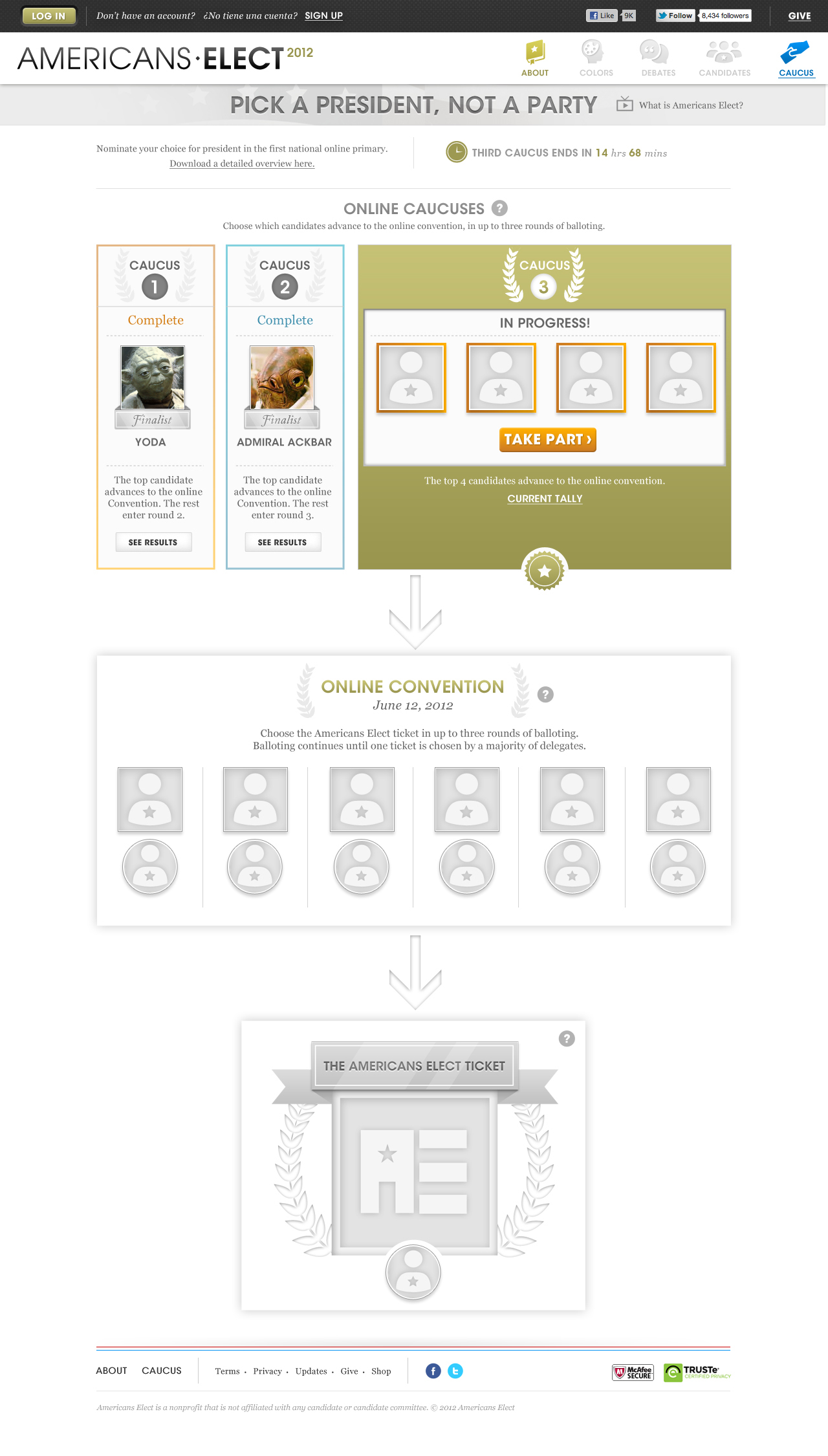
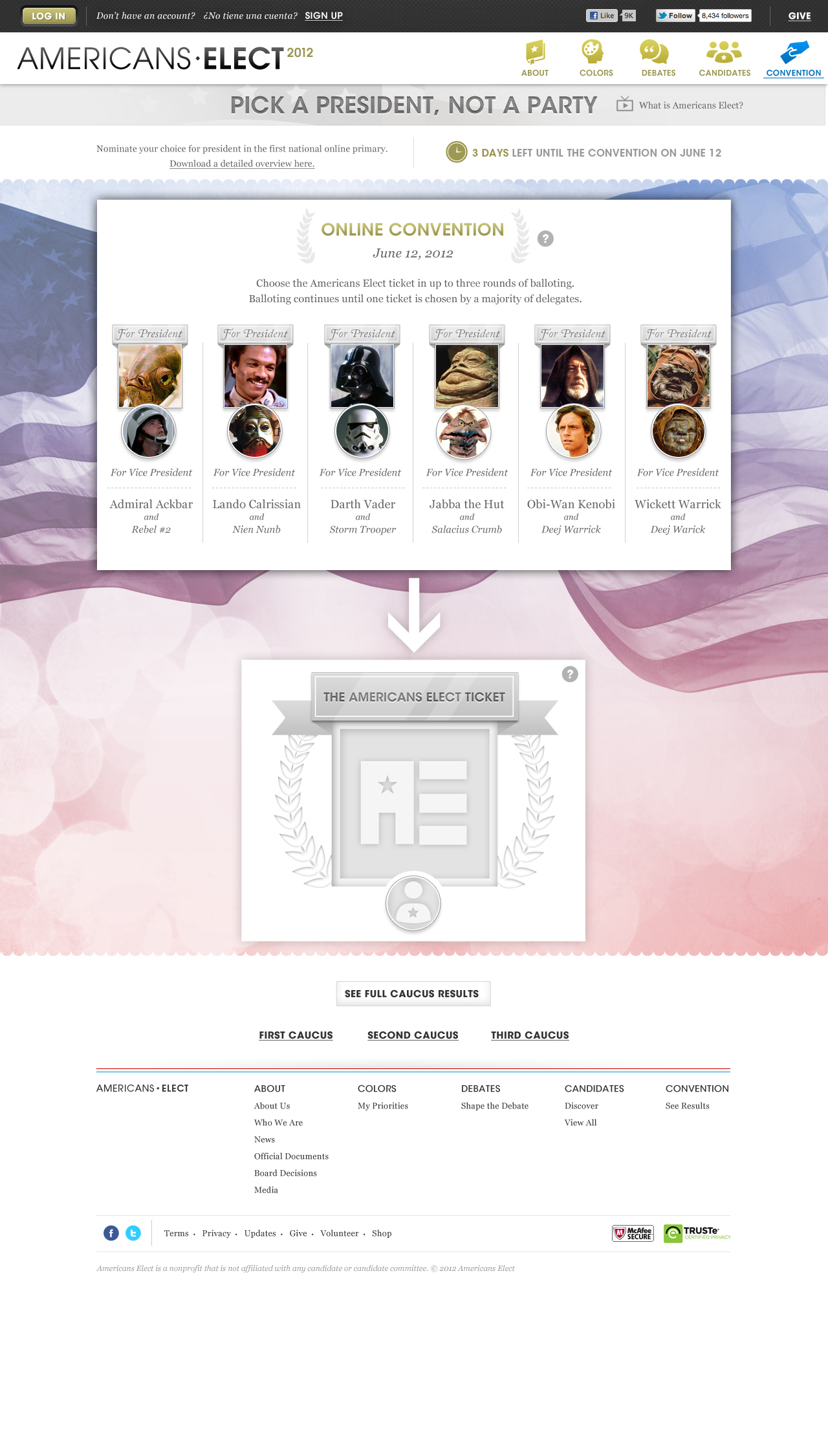
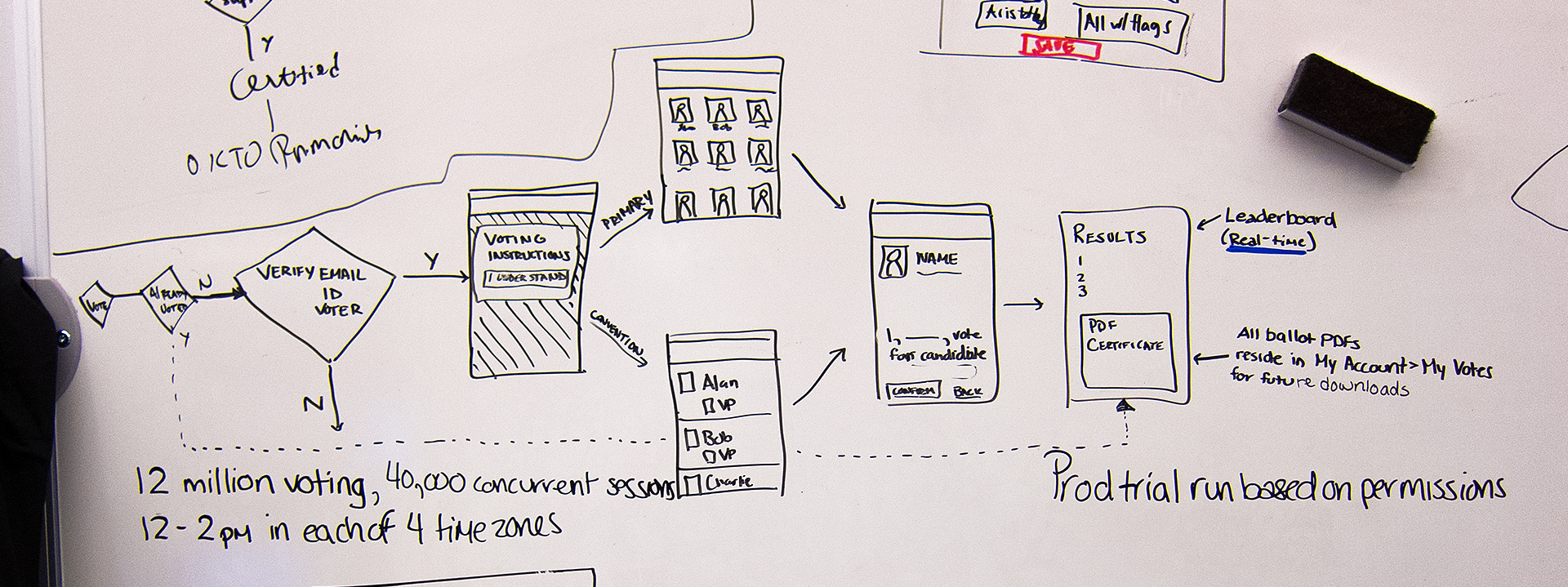
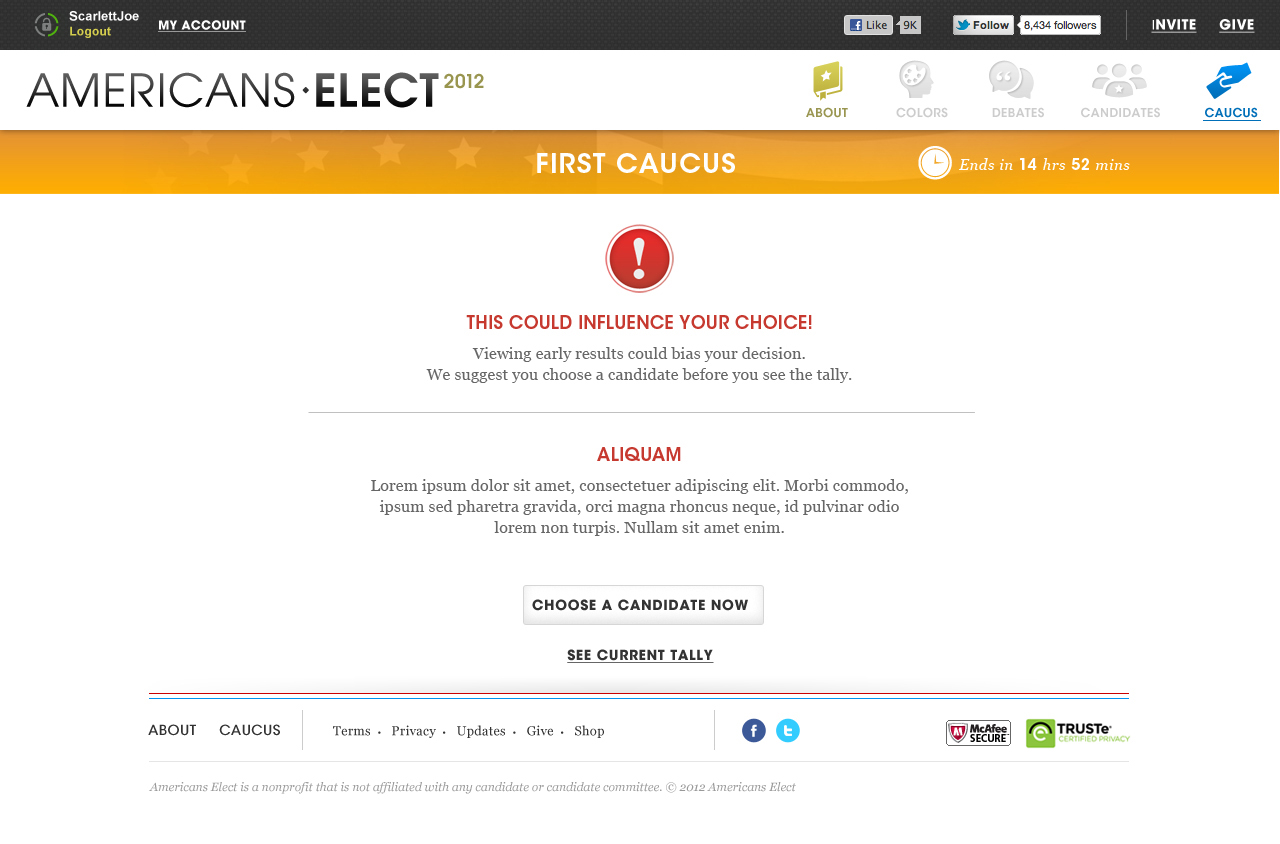
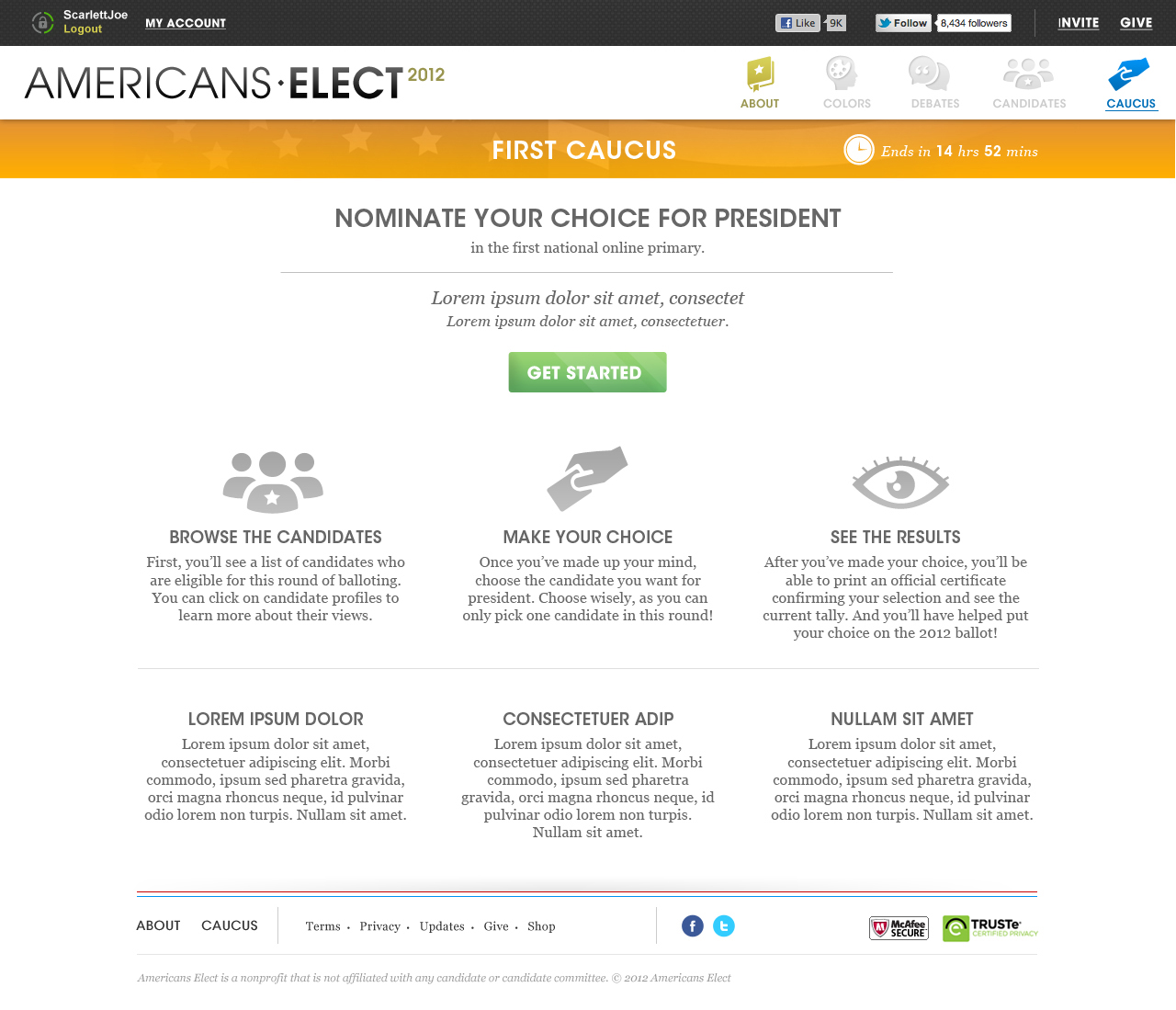
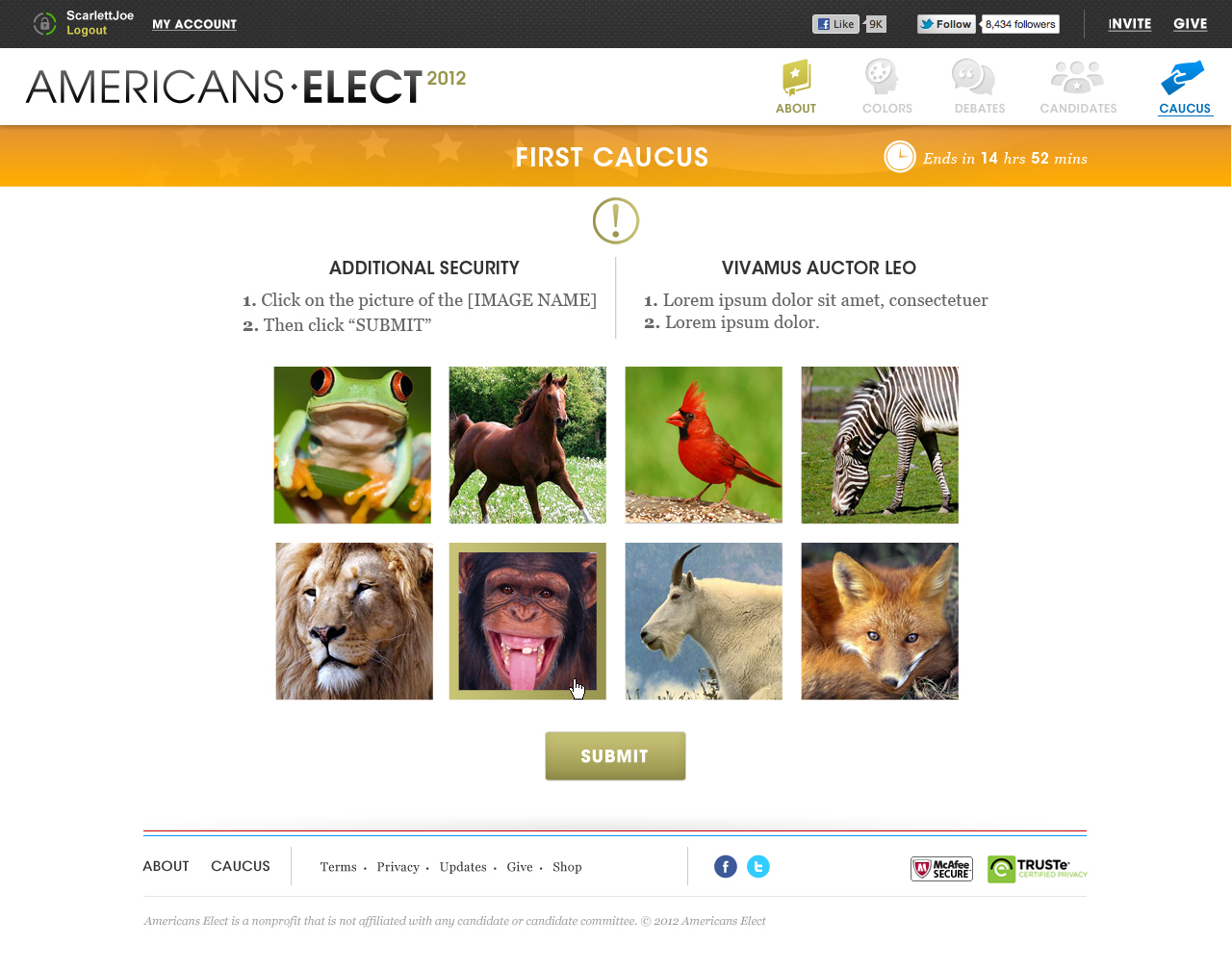
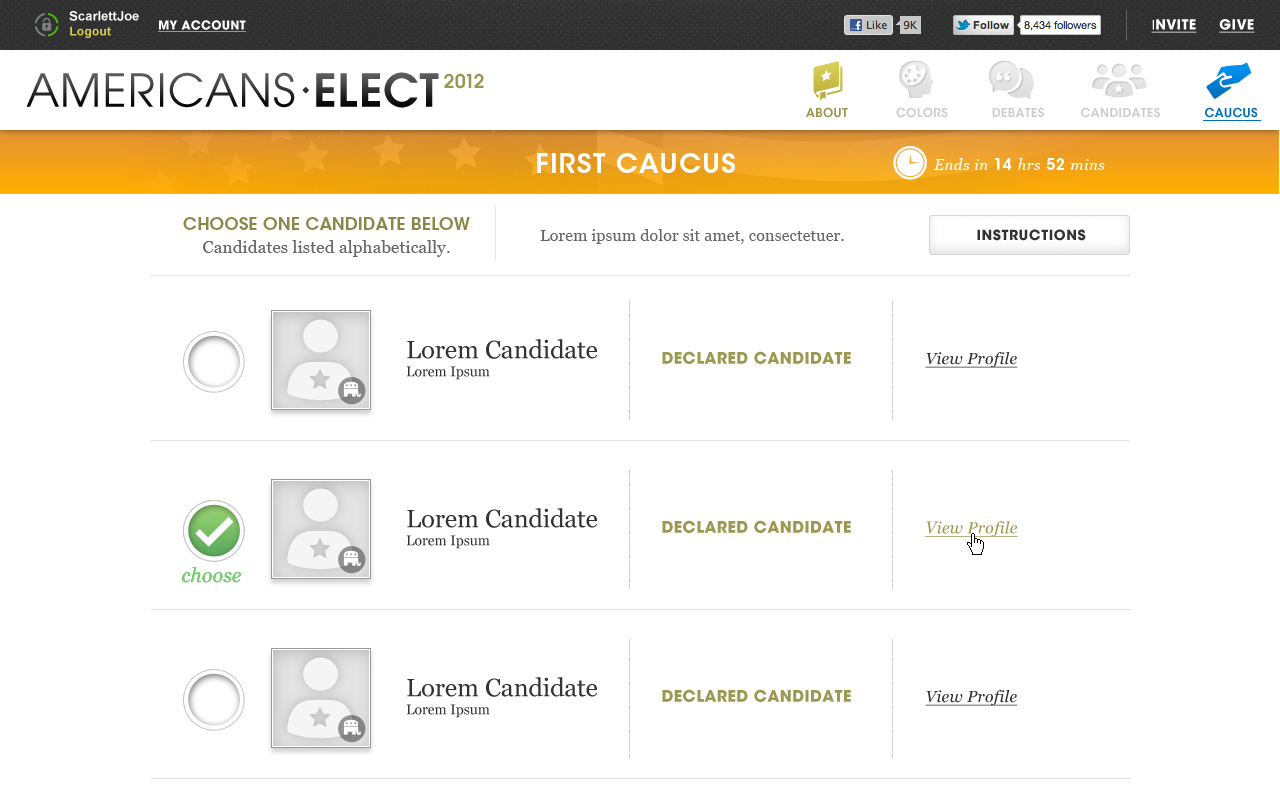
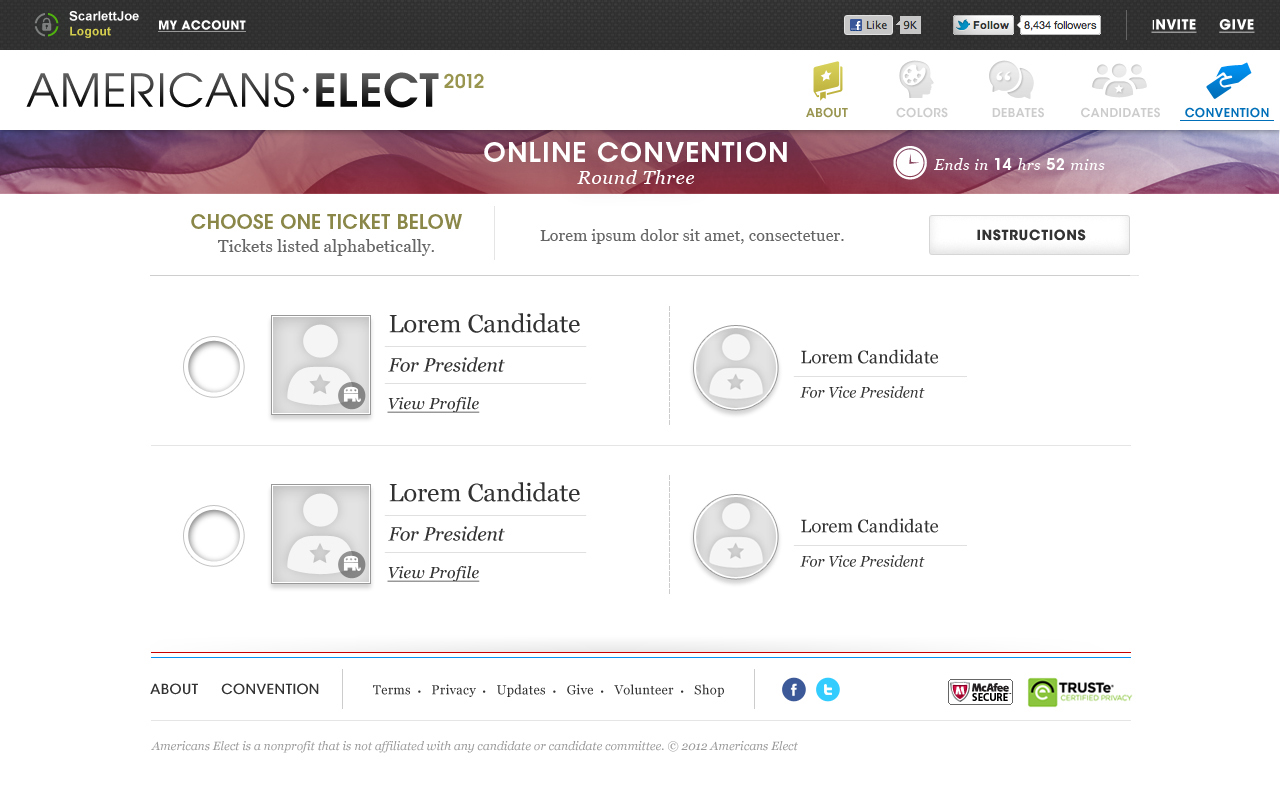
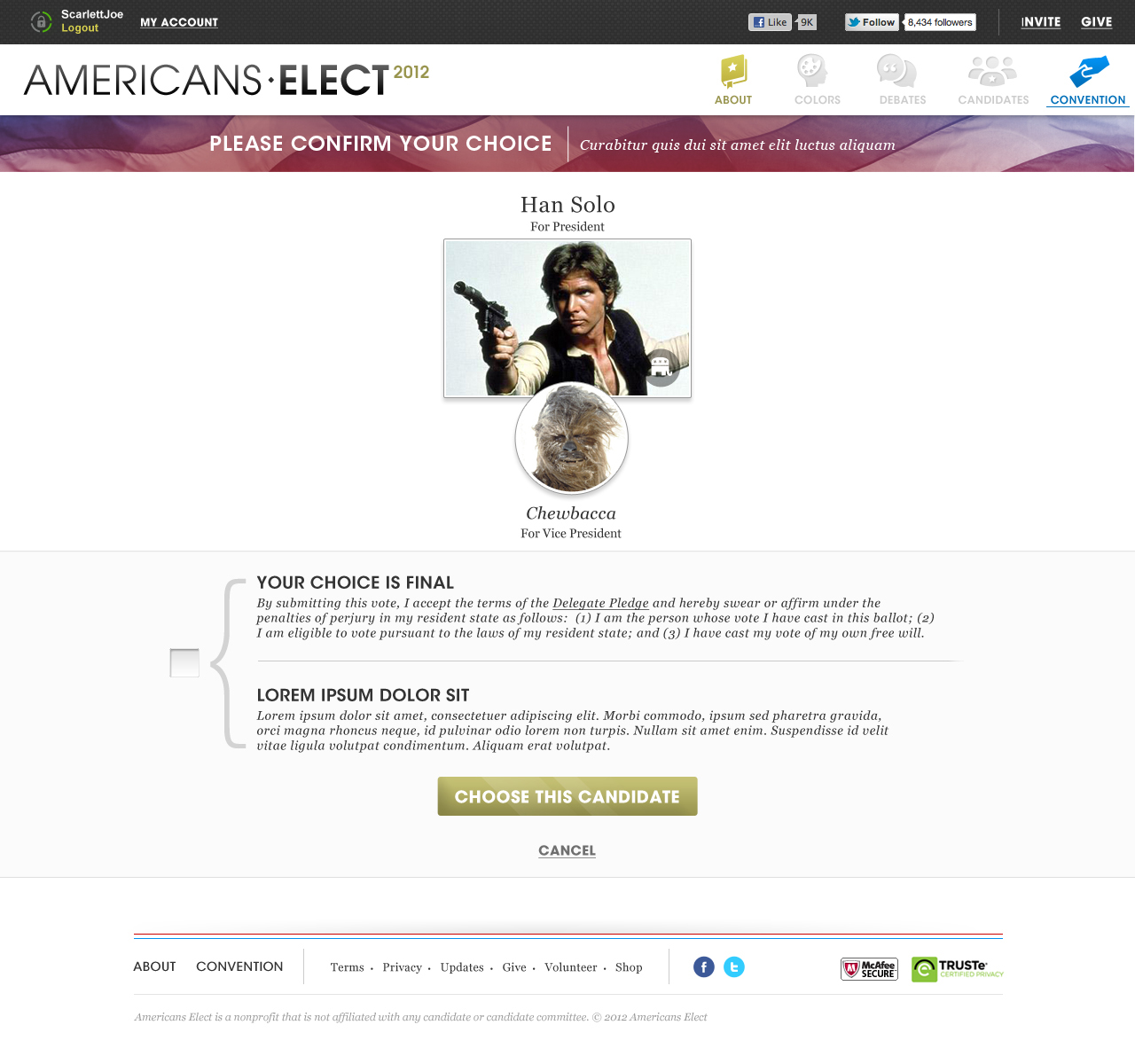
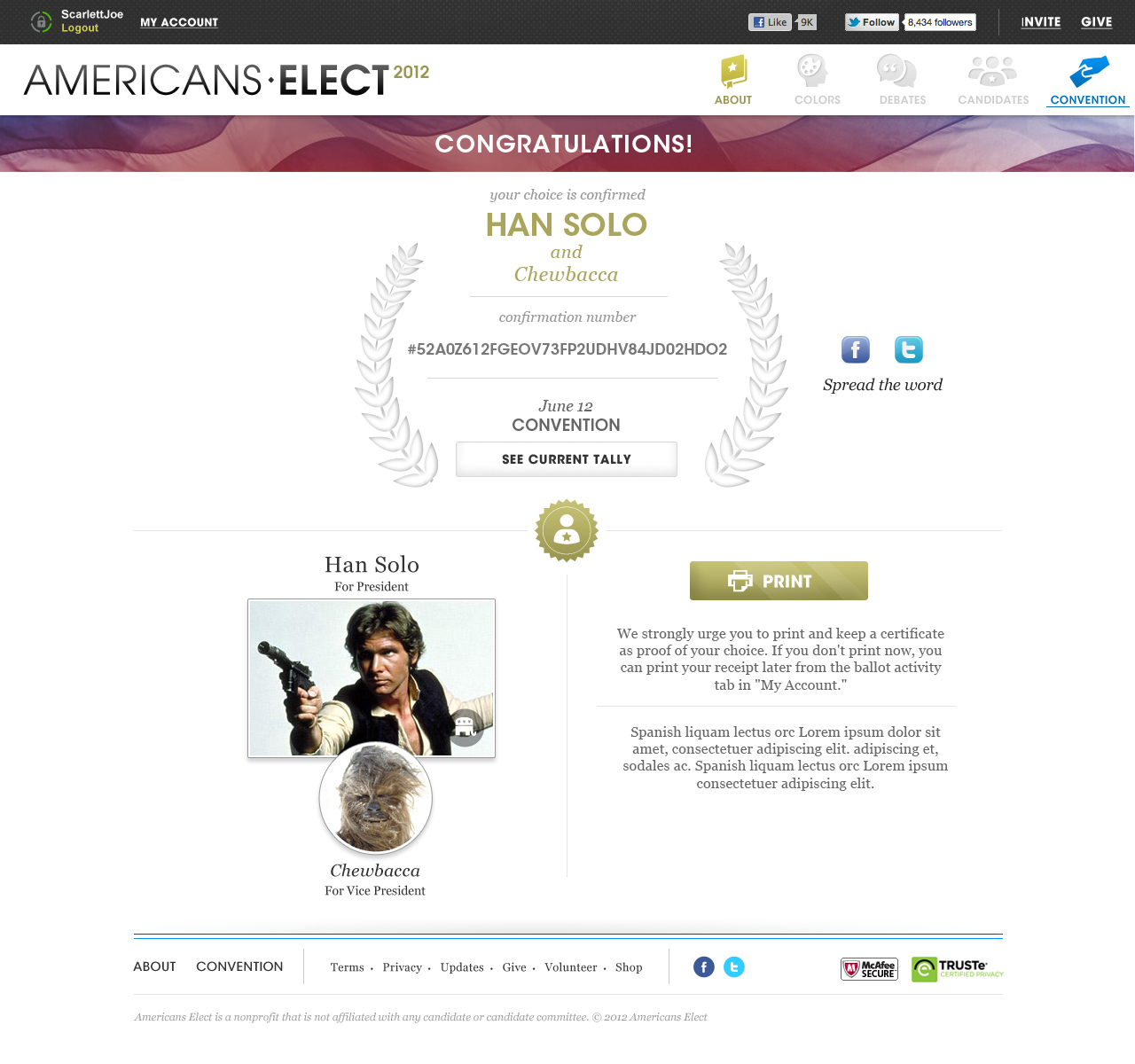
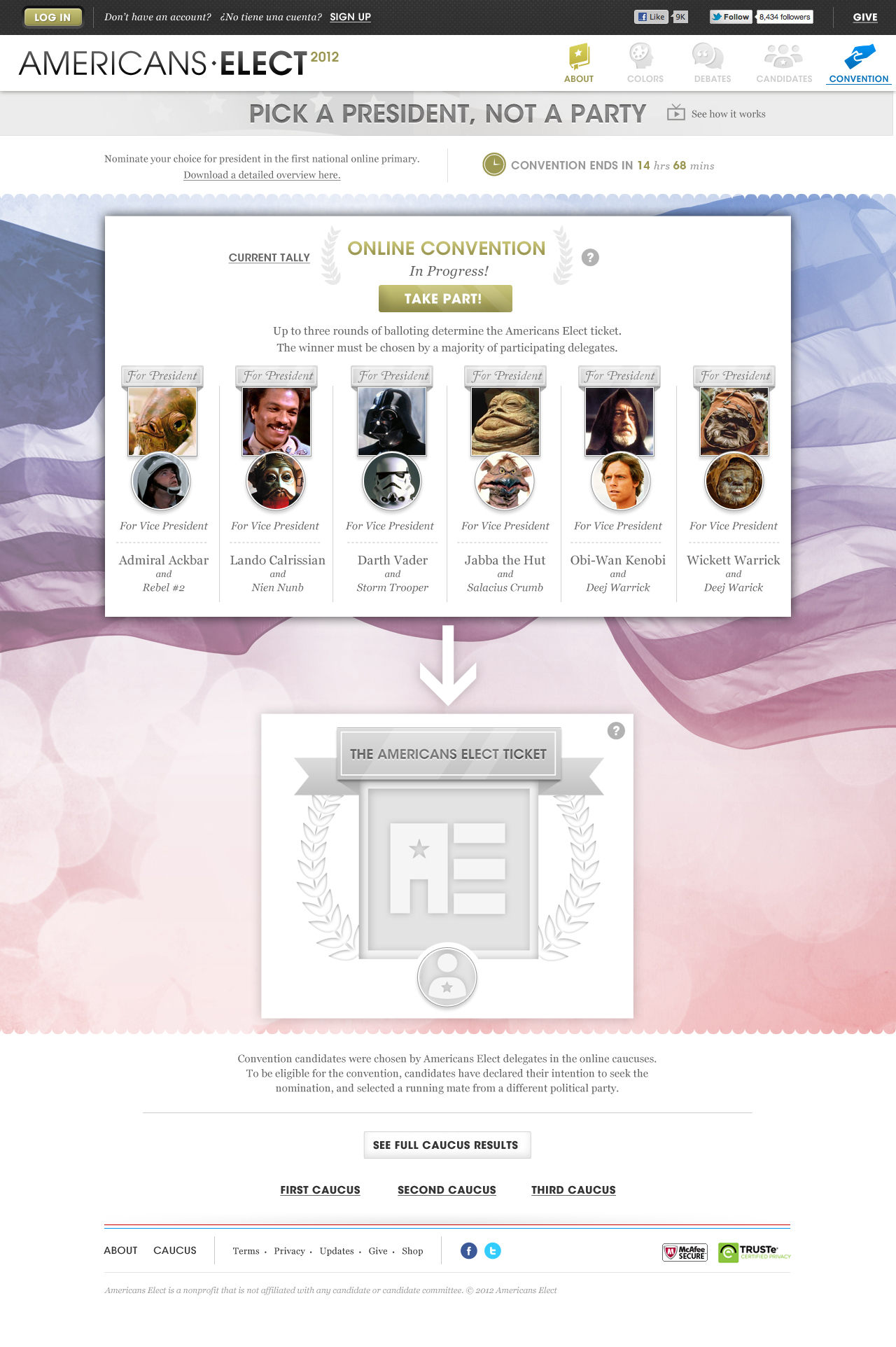
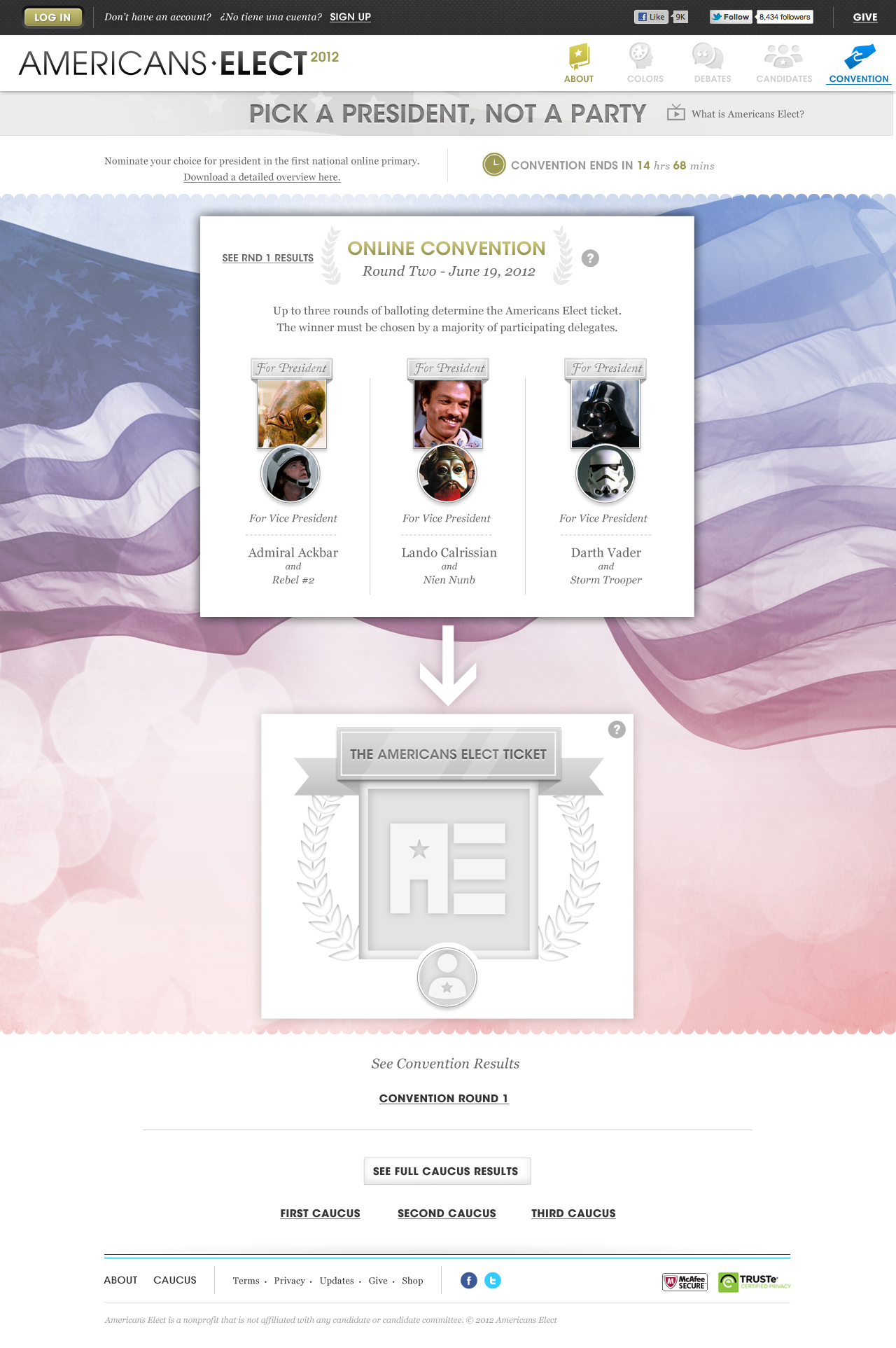
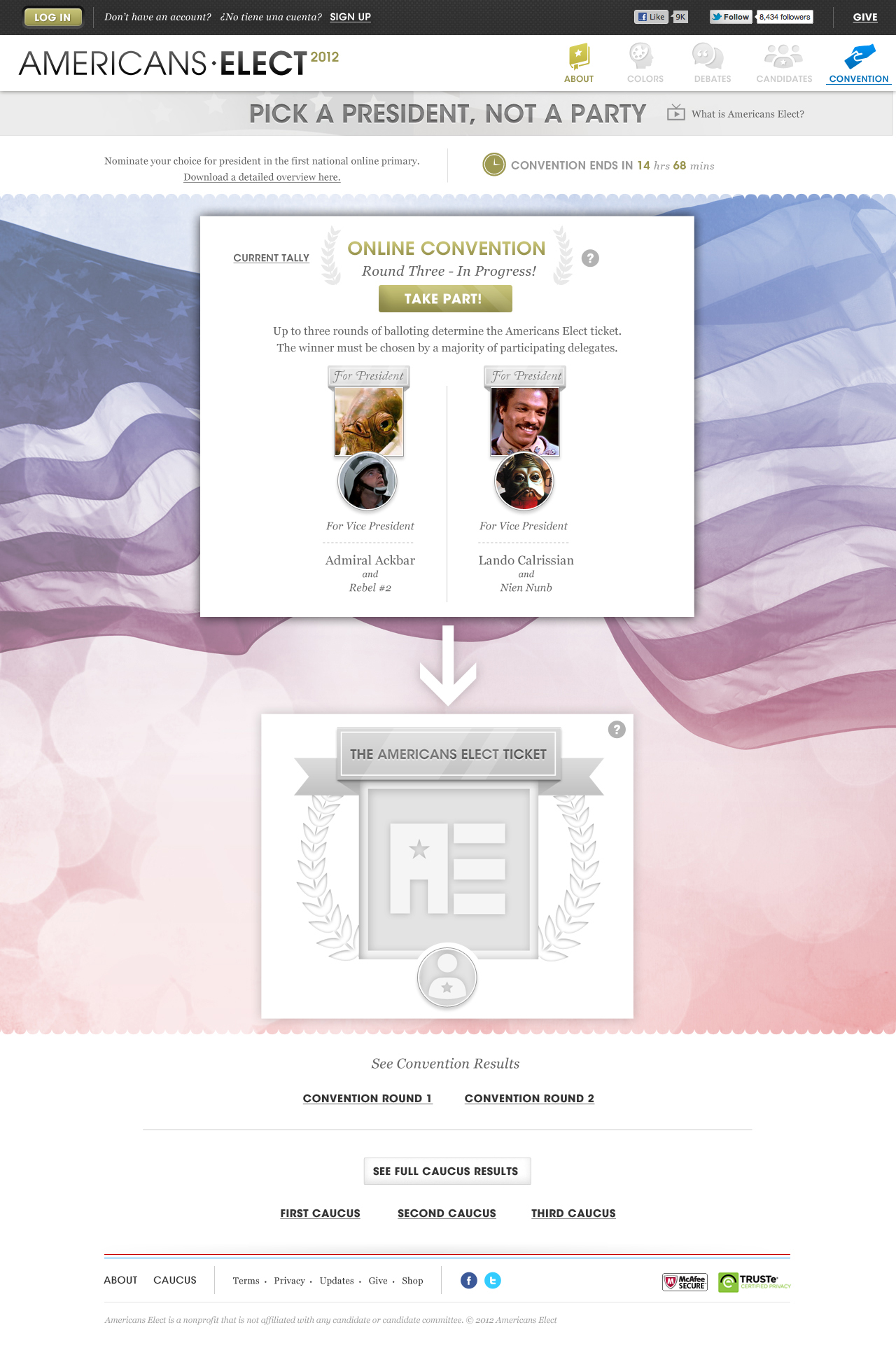
AMERICANS ELECT: THE FIRST EVER NATIONAL ONLINE PRIMARY
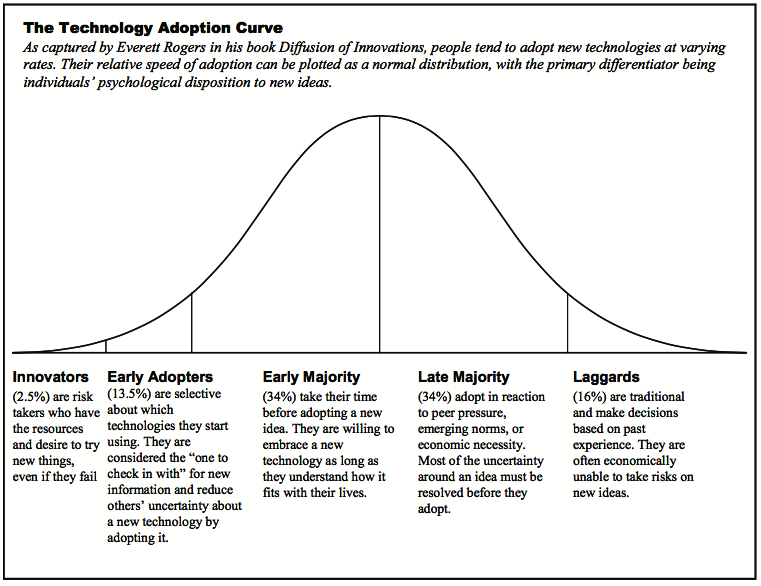
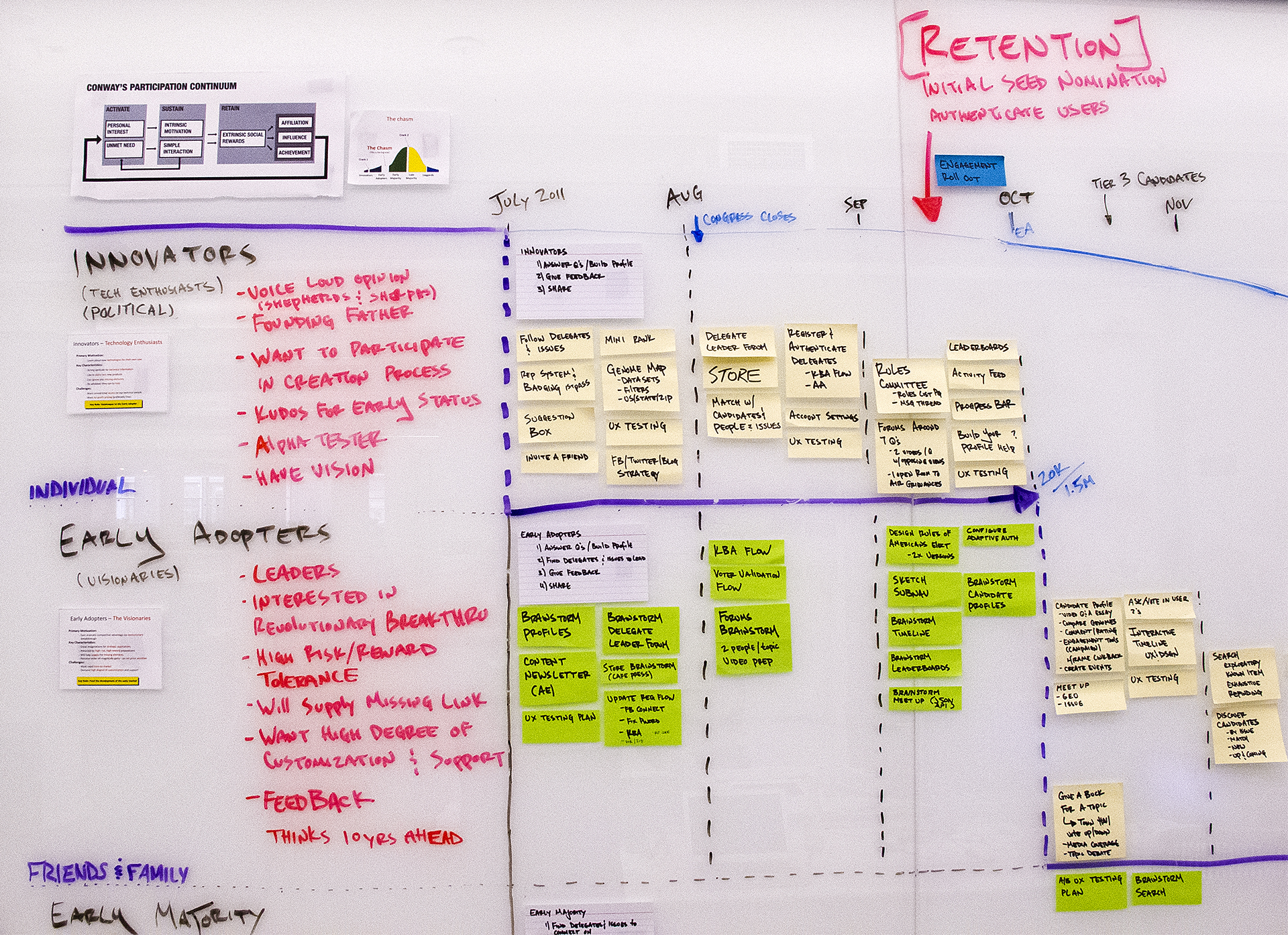
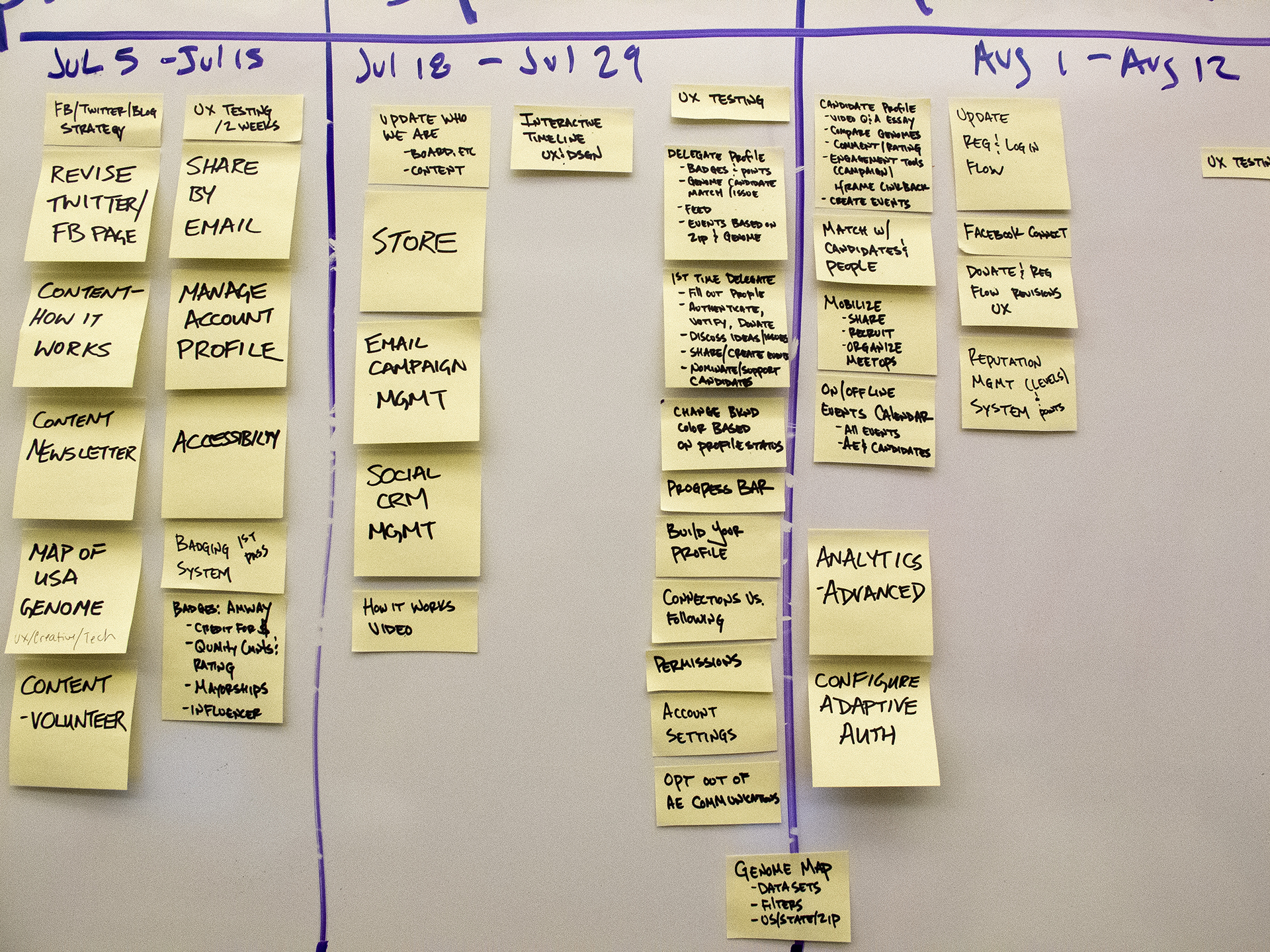
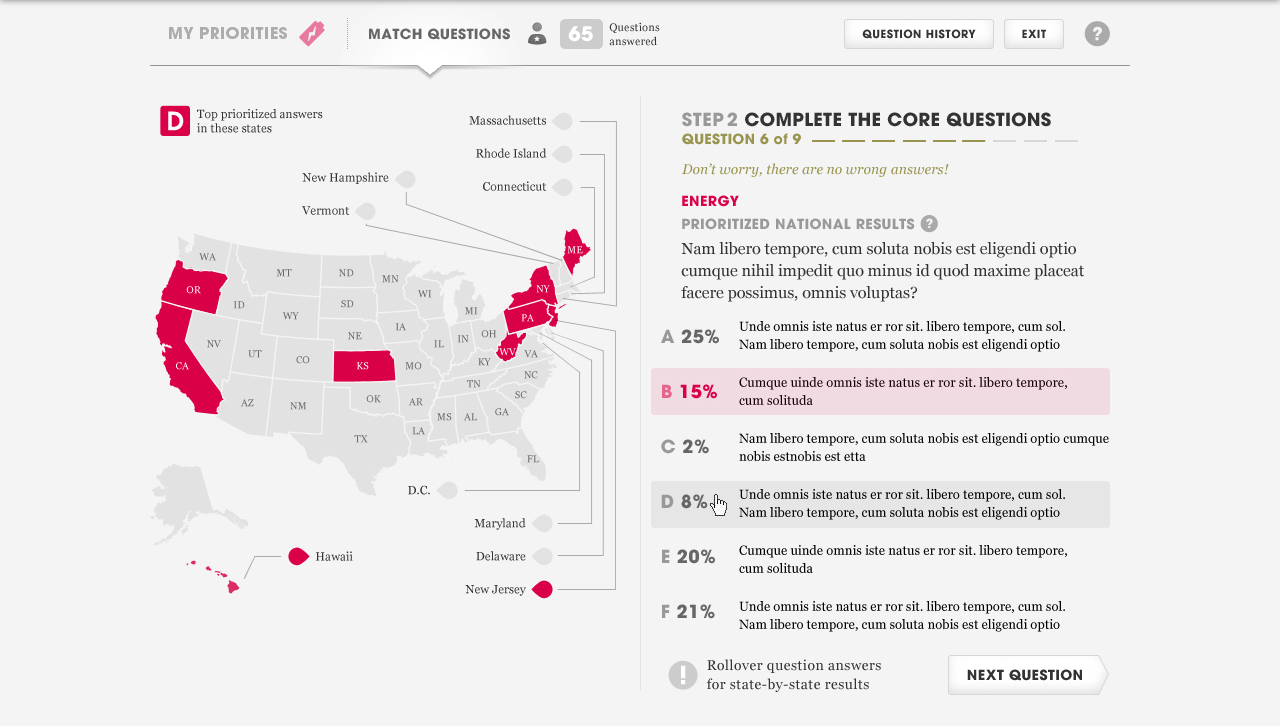
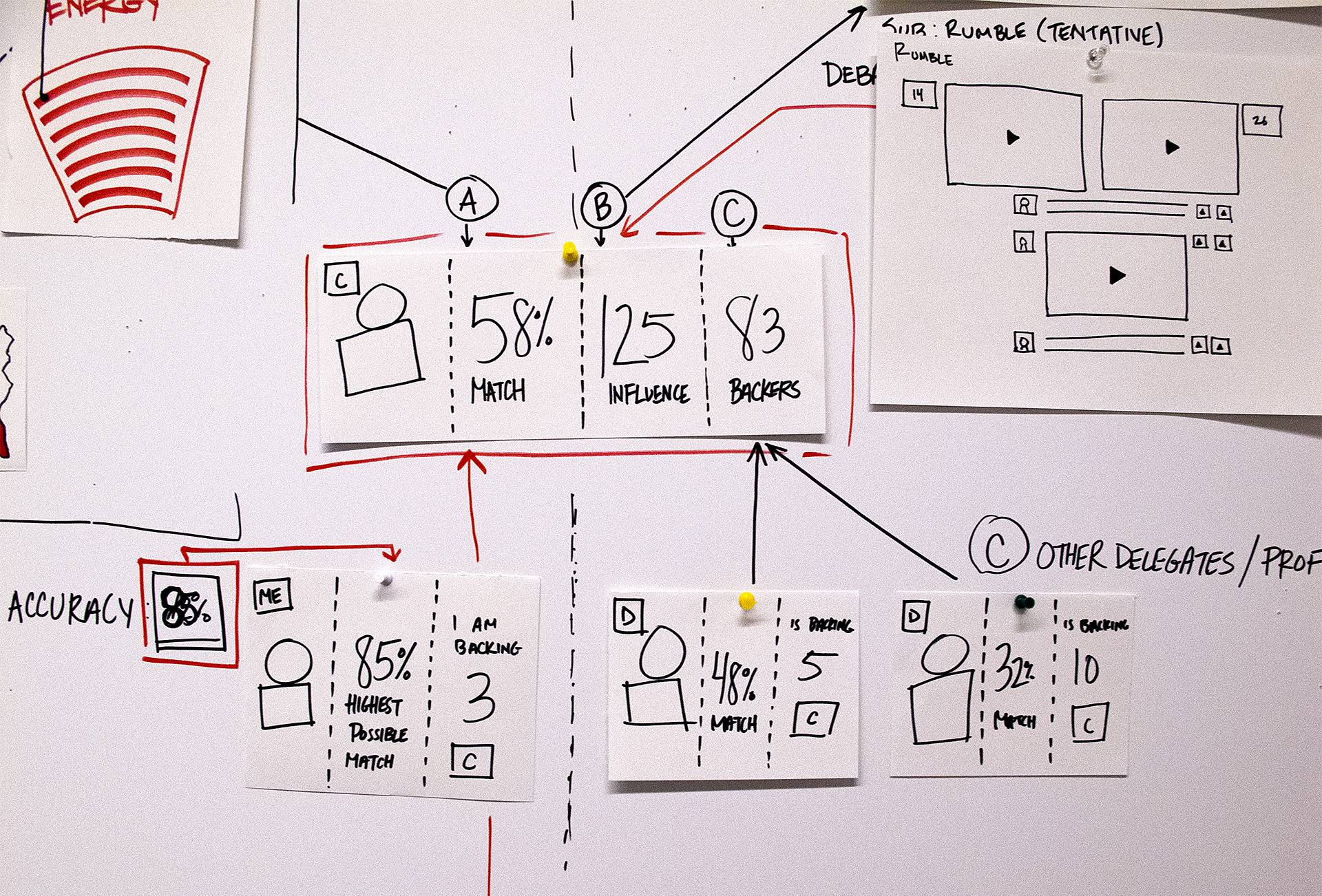
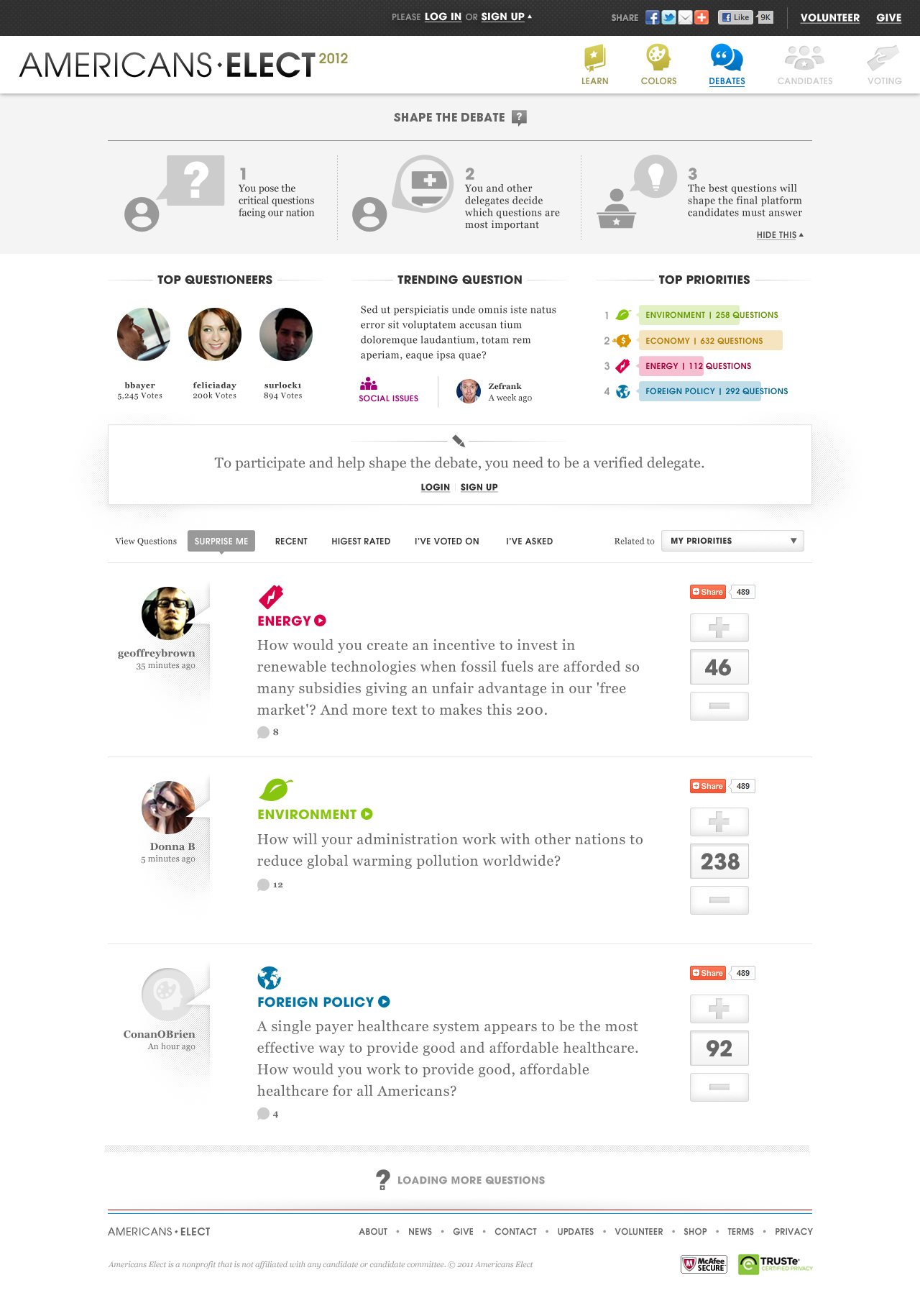
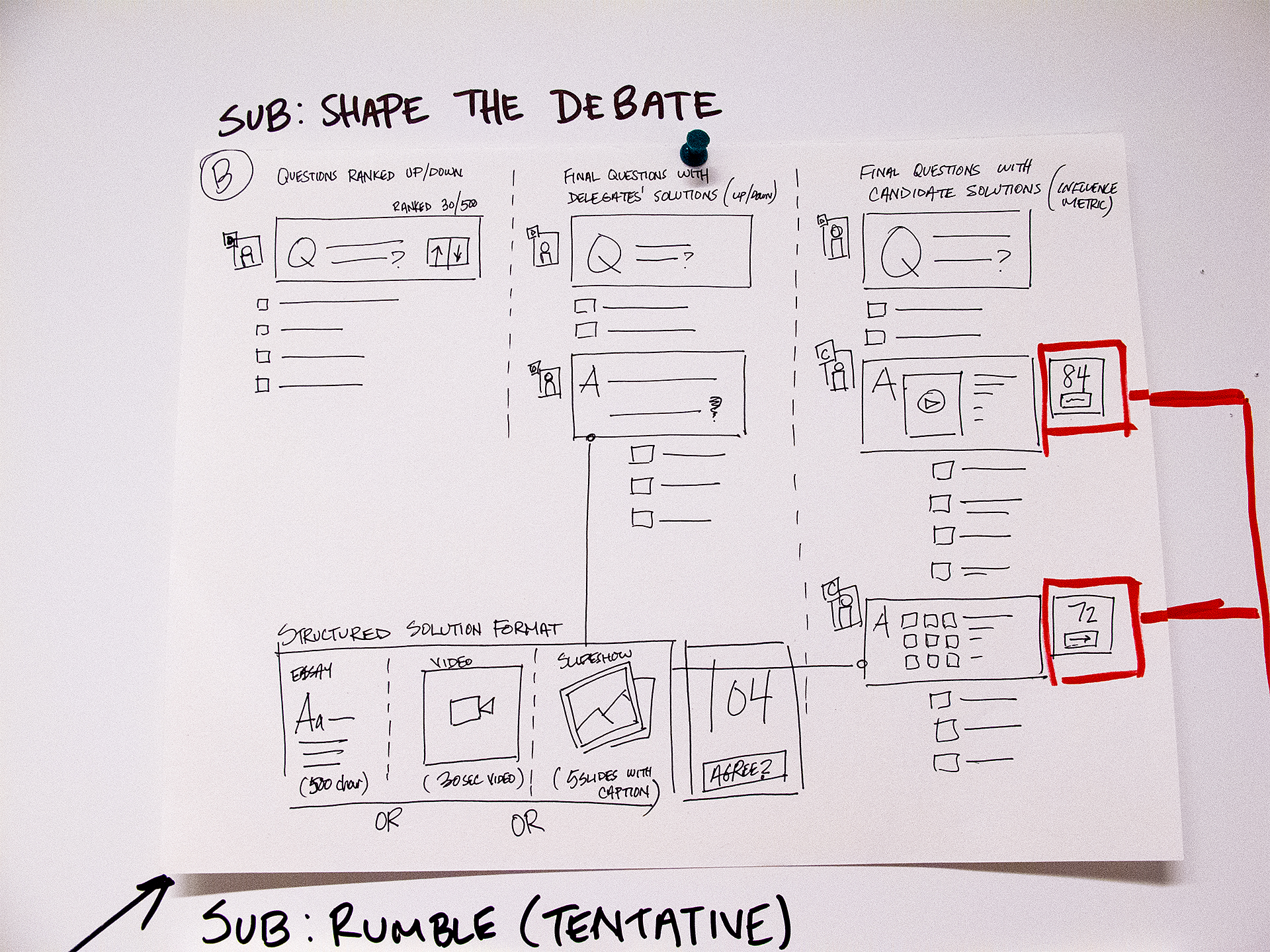
During the 2012 election cycle, Americans Elect asked if billions of dollars are transacted across the web every day, why can’t we vote on the internet? What was created was a new way to nominate and elect a presidential ticket.